Threat Hunting: Challenge 2 - CTF Challenge Writeup
Challenge Information
- Name: Threat Hunting: Challenge 2
- Objective: The objective of the “Threat Hunting: Challenge 2” CTF challenge is to identify the SHA256 hash value of the executable responsible for exfiltrating data within a given context.
Solution
To successfully tackle the “Threat Hunting: Challenge 2” challenge, I followed these steps:
Challenge Context:
- This challenge is part of a series in the threat hunting category and requires identifying the SHA256 hash value of the executable responsible for data exfiltration.
- It is recommended to solve Challenge 1 before looking into Challenge 2 and Challenge 3
- However, you can solve Challenge 2 and Challenge 3 in any order
Identifying Suspicious Executables:
On further inspection from the first challenge, I discovered a total three suspicious files including the one from the first challenge.
I dumped the two executables onto VirusTotal and HybridAnalysis, whilst analysed the powershell script myself.
The powershell script showed symptoms of reading files and encrypting it and I am suspecting that this is the file they are looking for, but not 100% certain.
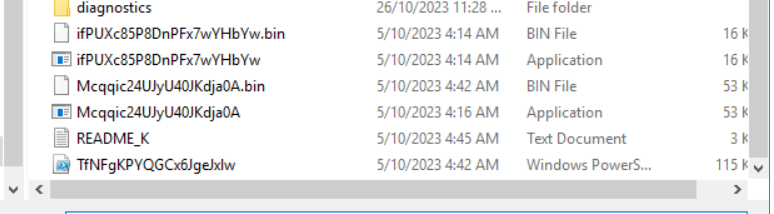
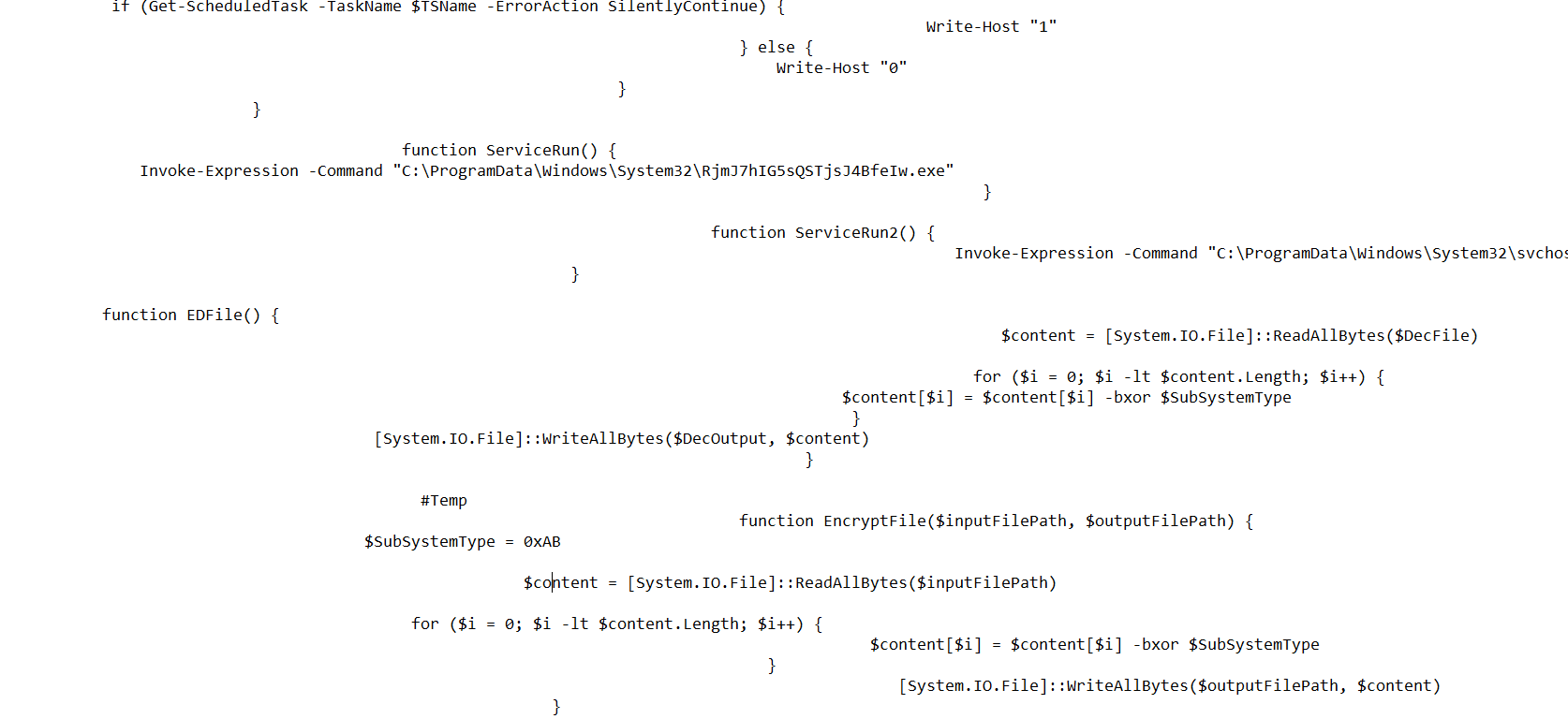
Approach to Finding SHA256 Hash:
- A common misconception might lead one to use
Get-FileHashto find the hash value. However, in challenges like these, this method may not yield the expected results. - This difference in hash values can be due to various factors and is further explained in this Stack Overflow thread.
- A common misconception might lead one to use
Using Hasher Tool:
- To accurately acquire the SHA256 hash value of the suspicious files, I utilized the Hasher tool available at Eric Zimmerman’s website.
Determining Executable’s SHA256 Hash:
- Since there were only three suspicious files discovered, and I am not so sure about my discovery, I will be calculating the SHA256 hash value for each of them using the Hasher tool and submitting as a flag.
Final Flag Discovery:
Among the calculated SHA256 hash values, one matched the expected format of the flag:
ABOH{hash_value}.At the time of writing this writeup, I have forgotten which one was the flag. Im sorry.
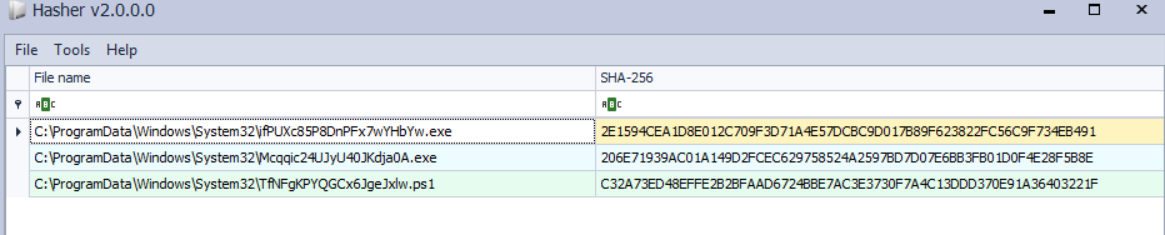
The resolution of the “Threat Hunting: Challenge 2” involved identifying potentially malicious executables and determining their SHA256 hash values using the Hasher tool to extract the flag.
Flag
The flag for this challenge is: ABOH{hash_value}.
This writeup illustrates the process of identifying the SHA256 hash value of a potentially malicious executable in the “Threat Hunting: Challenge 2” CTF challenge. For further inquiries or clarifications, feel free to ask.