SimpleLazy CTF Challenge Writeup
Challenge Information
- Name: SimpleLazy
- Points: 330
- Category: Web
- Objective: The challenge involves exploiting a Local File Inclusion (LFI) vulnerability to retrieve a flag.
Solution
Here’s a detailed solution for the SimpleLazy CTF challenge:
Initial Assessment:
Immediately recognized the challenge as having a Local File Inclusion (LFI) vulnerability, particularly with the
page3.phpparameter.Discovered that input was always appended with
.php, limiting directory traversal options.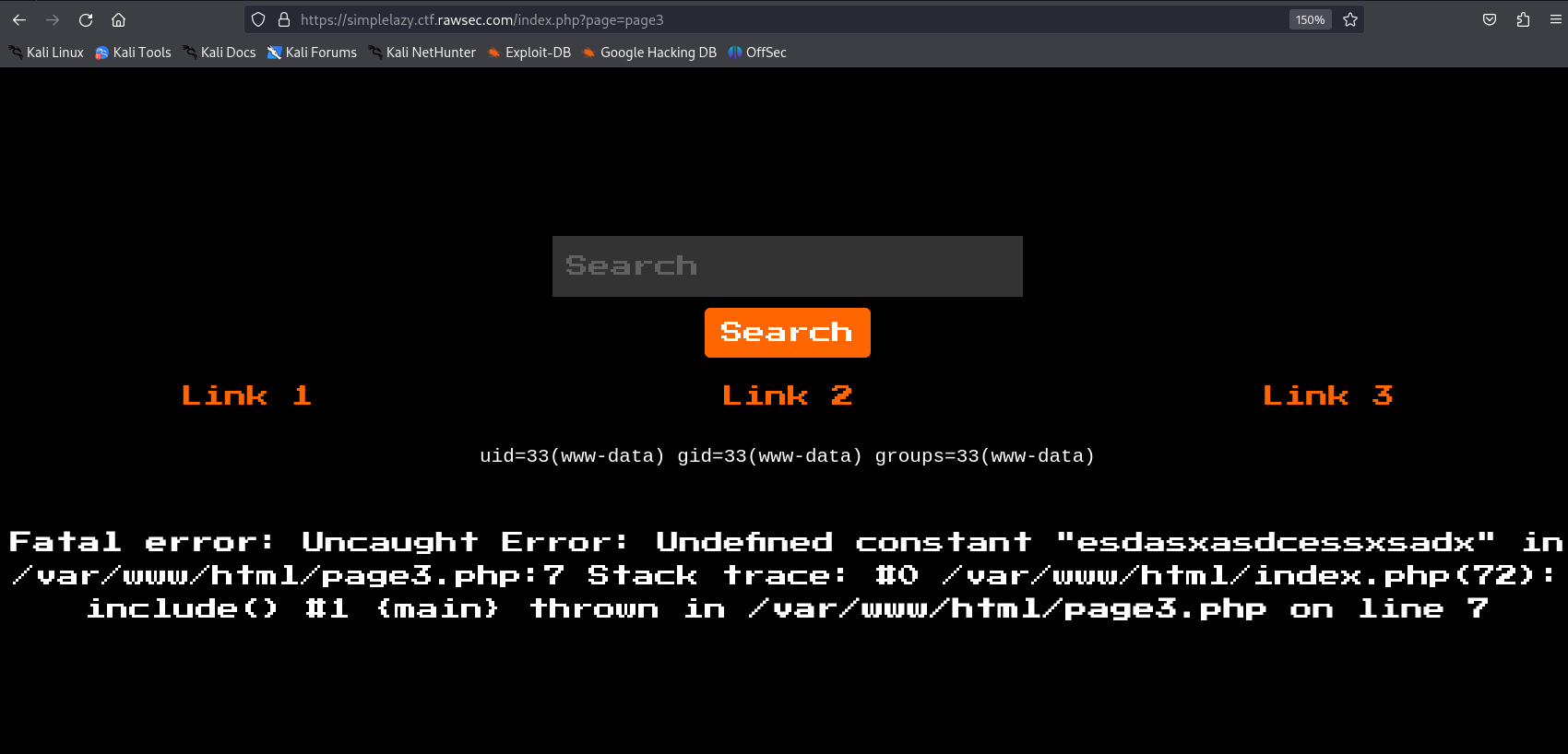
Strategy for Exploitation:
Focused on extracting PHP source code from
index.php,page1.php,page2.php, andpage3.php.Utilized
php://filterto retrieve PHP files in base64 format, allowing for remote file inclusion.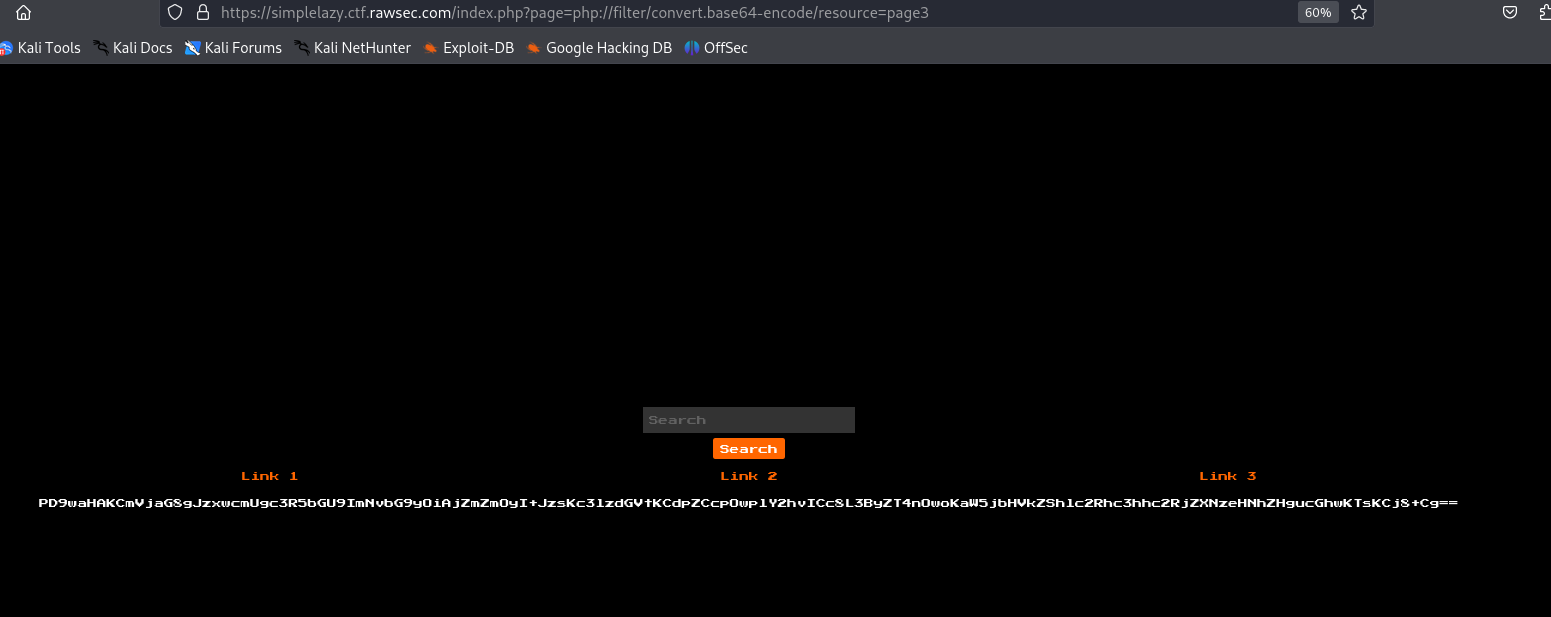
Exploiting the LFI:
Retrieved the source code of
page3.phpusingphp://filter.Discovered the inclusion of a suspicious file in the PHP source code.
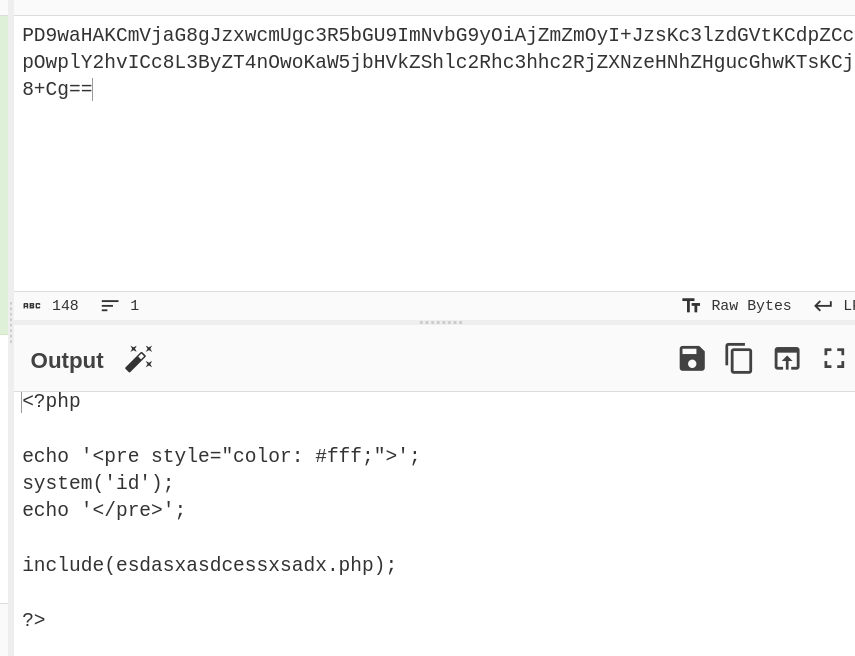
Retrieving the Flag:
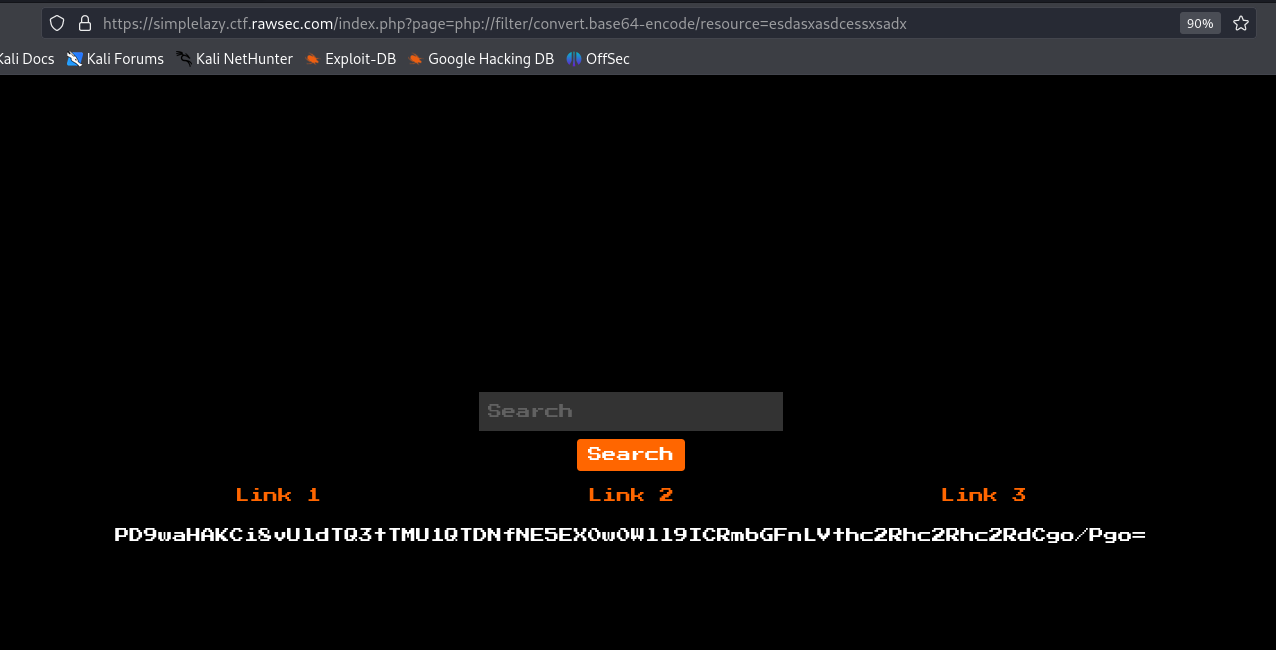
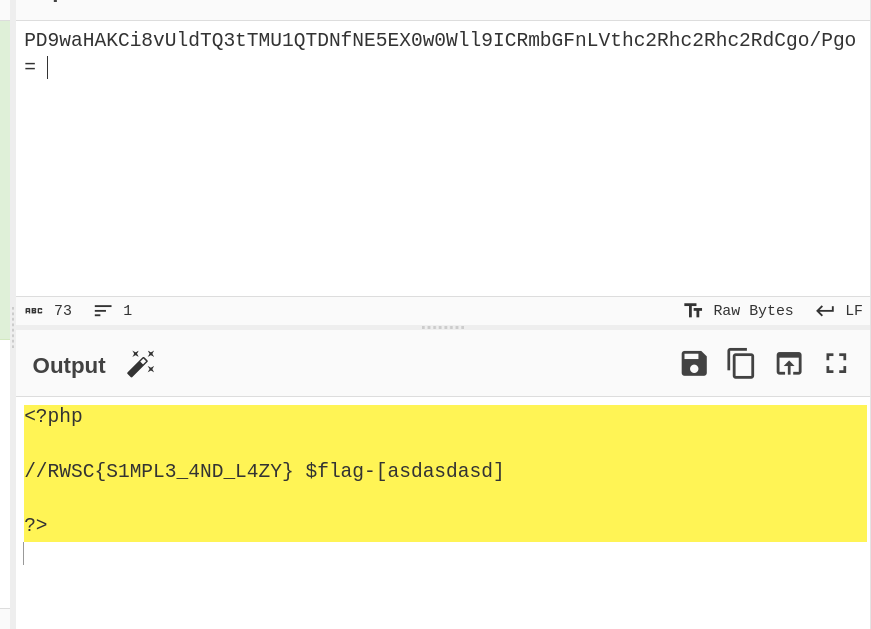
Applied the same
php://filtertechnique to extract the suspicious file’s contents in base64 format.Decoded the contents of the suspicious file to reveal the flag.
Conclusion
The SimpleLazy CTF challenge demonstrated the importance of understanding LFI vulnerabilities and using techniques like php://filter to retrieve PHP source code and extract hidden files. By exploiting the vulnerability and decoding the suspicious file’s contents, the flag was successfully obtained, completing the challenge.