Packman CTF Challenge Writeup
Challenge Information
- Name: Packman
- Points: 300
- Category: Reverse Engineering
- Objective: Reverse engineer a Python-compiled Windows executable to retrieve a flag.
Solution
File Enumeration:
- Upon receiving the reverse engineering file, the first step was to enumerate the details.
- The filename indicated it was a Windows executable due to the
.exeextension.
Identifying the Binary Type:
By running the
stringscommand on the file, I identified it as a Python-compiled executable rather than one compiled with C, C++, or Rust.The presence of Python libraries and mentions of
pycandpyzin the output confirmed this.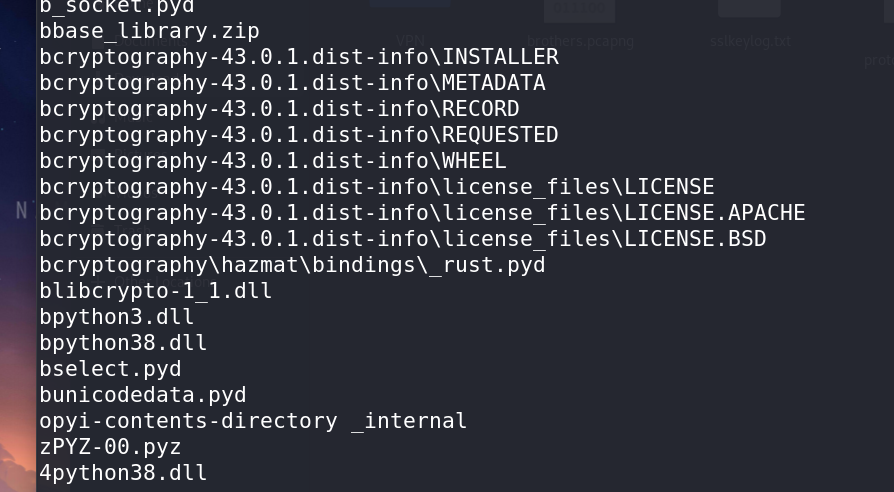
Decompilation Process:
- For Python-compiled binaries, the typical approach is to reverse it to obtain the original Python code.
- I utilized
pyinstxtractorto extract the.pycfile from the executable. - After obtaining the
.pycfile, I usedpycdcto convert the.pycback into readable Python code.
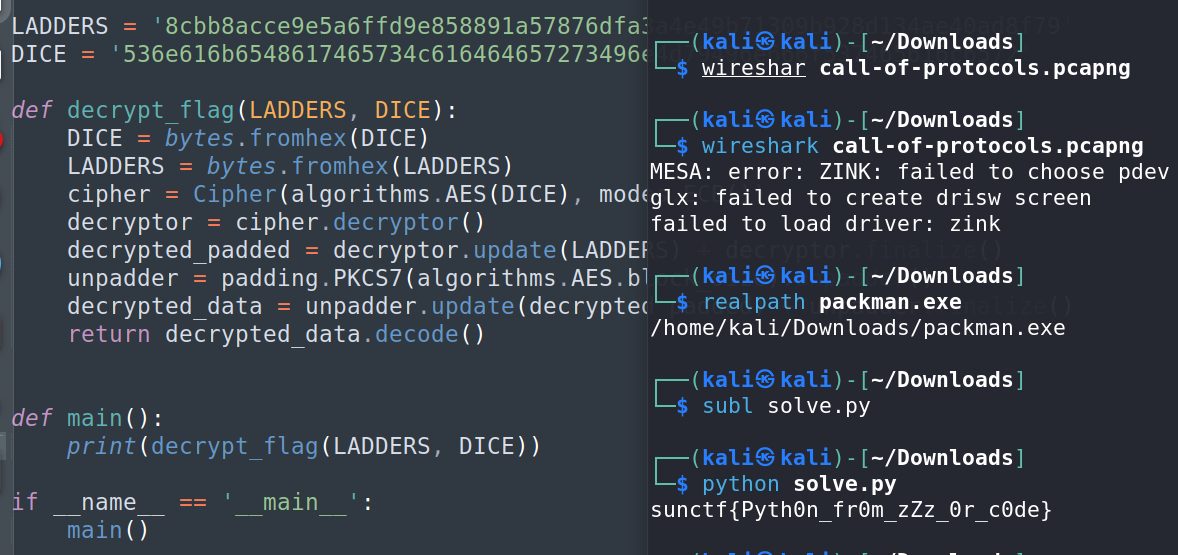
Flag Retrieval:
With the decompiled Python code, I searched through the functions and identified one that would generate or return the flag.
I executed the relevant function to retrieve the flag.