Notsus.exe CTF Challenge Writeup
Challenge Information
- Name: Notsus.exe
- Points: 100
- Category: Forensics
- Objective: Analyze and decrypt files extracted from a ZIP archive using a known plaintext attack and reverse engineer a bundled Python executable to extract the final flag.
Solution
Understanding the Challenge:
- Provided with a ZIP-based executable (
dist-notsus.exe) that, when unzipped, throws a bunch of errors. - From prior experience, this behavior hints at a classic PKZIP encryption challenge solvable with
bkcrack, a known plaintext attack tool.
- Provided with a ZIP-based executable (
Initial File Inspection:
Extracting the ZIP reveals two files:
notsus.exe— a Windows executable.flag.txt.yorm— a file with an unfamiliar.yormextension, likely custom or encrypted.
The path of least resistance is to first target the
.exe, since the standard DOS executable header often contains a predictable string:1This program cannot be run in DOS mode.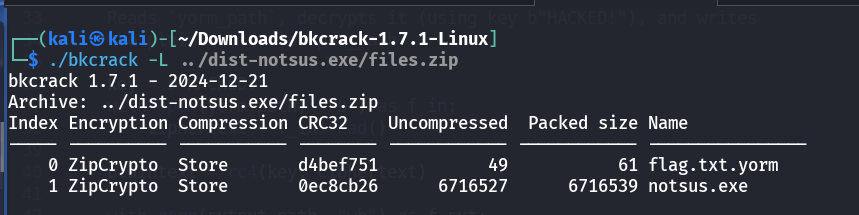
Identifying the Known Plaintext Offset:
The known string appears mid-file, not at the start. Therefore, the correct offset is crucial.
Use the command to locate it:
1grep -aob $'\x21This program' known.exeThis returns the byte offset (e.g.,
78) which will be passed tobkcrack.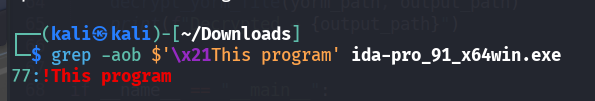
Preparing for Known Plaintext Attack:
Save the known plaintext string to a file:
1echo -ne 'This program cannot be run in DOS mode.\r\r\n' > exe_offset_plain.txtPerform the attack:
1./bkcrack -C ../dist-notsus.exe/files.zip -c notsus.exe -p exe_offset_plain.txt -o 78This reveals the internal encryption keys:
d1608c35 d11d350a 4bc3da9c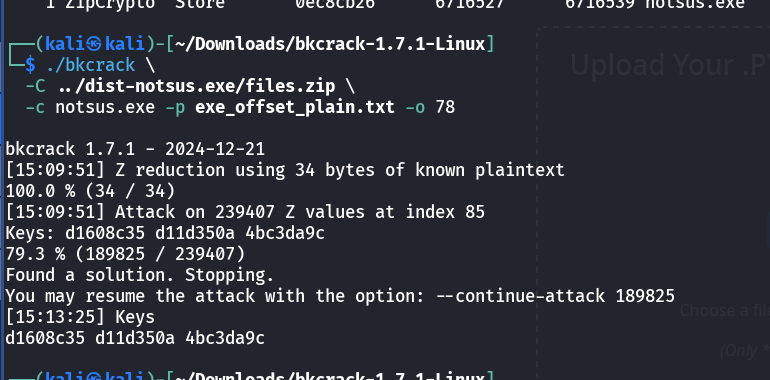
Decrypting the ZIP Contents:
- Use the recovered keys to fully decrypt both files:
1 2./bkcrack -C ../dist-notsus.exe/files.zip -c notsus.exe -k d1608c35 d11d350a 4bc3da9c -d notsus.exe ./bkcrack -C ../dist-notsus.exe/files.zip -c flag.txt.yorm -k d1608c35 d11d350a 4bc3da9c -d flag.txt.yorm
- Use the recovered keys to fully decrypt both files:
Reverse Engineering
notsus.exe:The executable is actually a Python program bundled using PyInstaller.
Use the following tools to extract and decompile the executable:
- Pyinstxtractor
- Pylingual (for decompiling .pyc files)
Analyzing the code reveals the logic to decrypt the
flag.txt.yormfile using a custom decryption routine.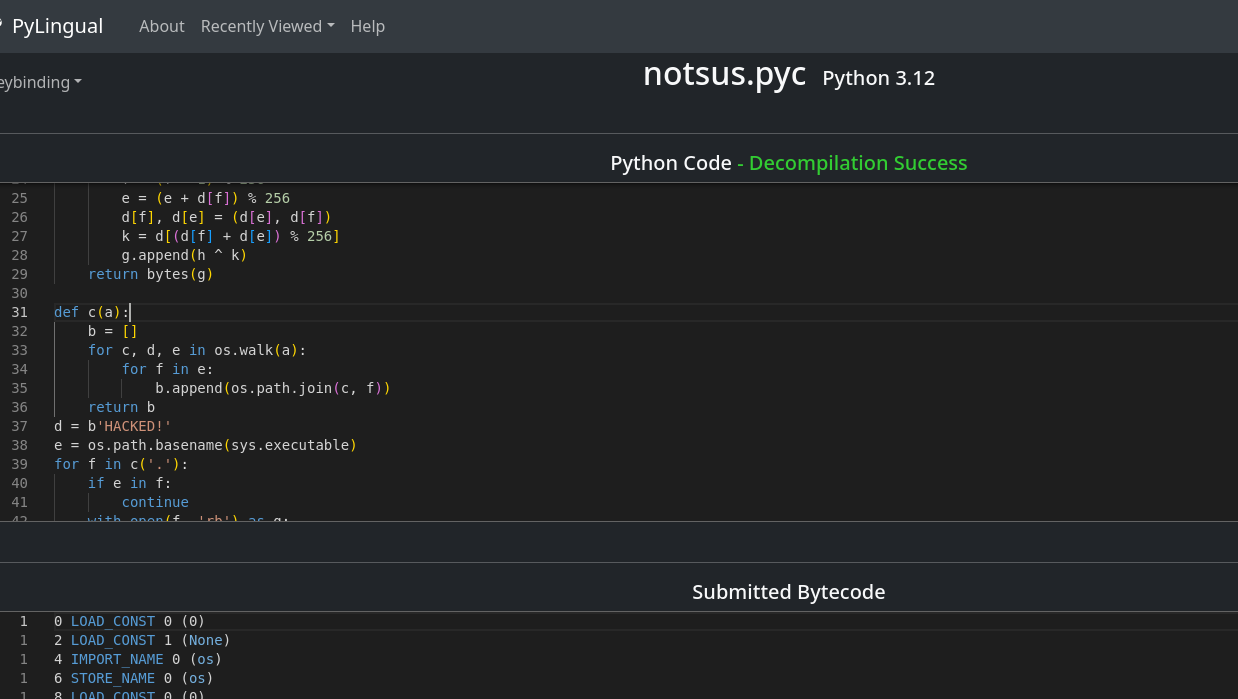
Decrypting the Flag File:
Re-implement the decryption algorithm based on the logic found in the decompiled script.
Running it on
flag.txt.yormreveals the flag.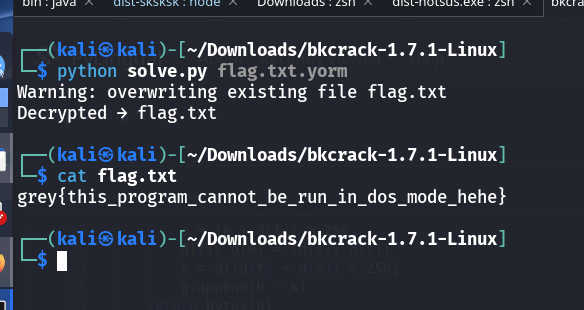
Flag
grey{this_program_cannot_be_run_in_dos_mode_hehe}