Mystery File CTF Challenge Writeup
Challenge Information
- Name: Mystery File
- Points: 500
- Category: DFIR (Digital Forensics and Incident Response)
- Objective: Deobfuscate a script within a ZIP file to uncover a domain and retrieve the flag from the associated webpage.
Solution
To solve the “Mystery File” challenge, follow these steps:
Initial Analysis:
We are given a file named
program.bin.Use the
filecommand to identify the nature of the file, which reveals it is a ZIP archive.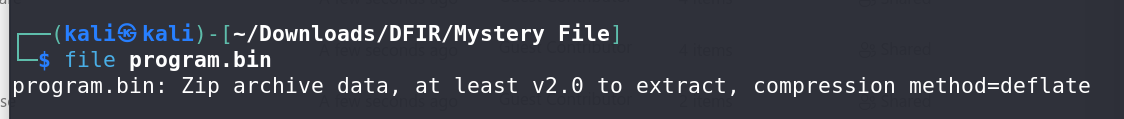
Extracting the ZIP File:
Unzip
program.binto obtain its contents, which include a large, obfuscated Bash script.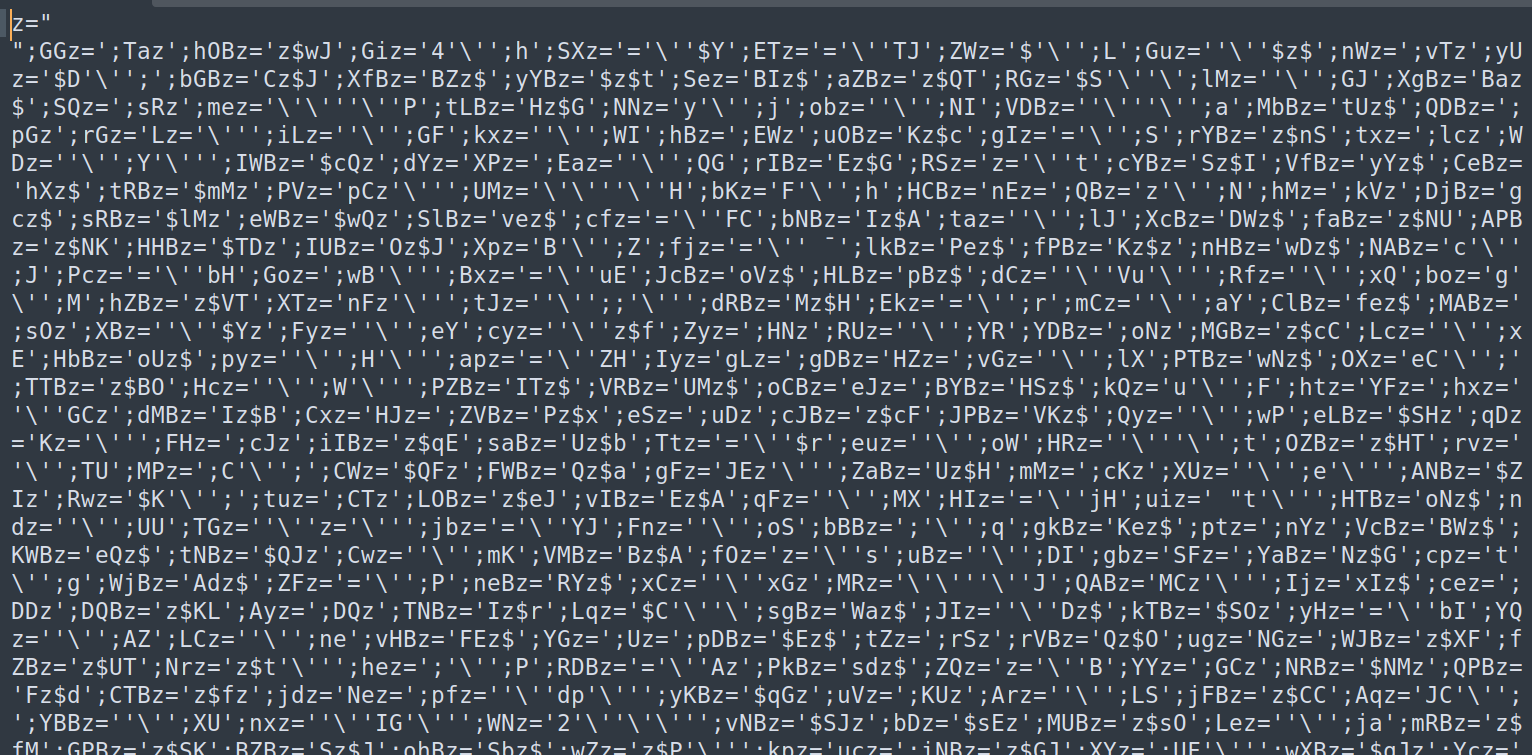
Running the Script:
To handle the obfuscation, use an online Bash interpreter such as TIO.run to execute the script.
The initial execution of the script shows no useful output.
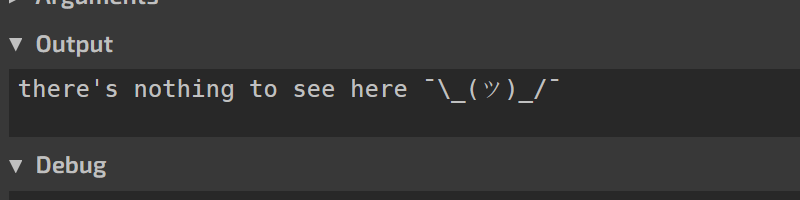
Deobfuscating the Script:
Modify the script to replace
evalwithecho. This allows you to see the script’s output, revealing a new, similarly obfuscated Bash script.Repeat the process of replacing
evalwithechoto progressively reveal less obfuscated versions of the script.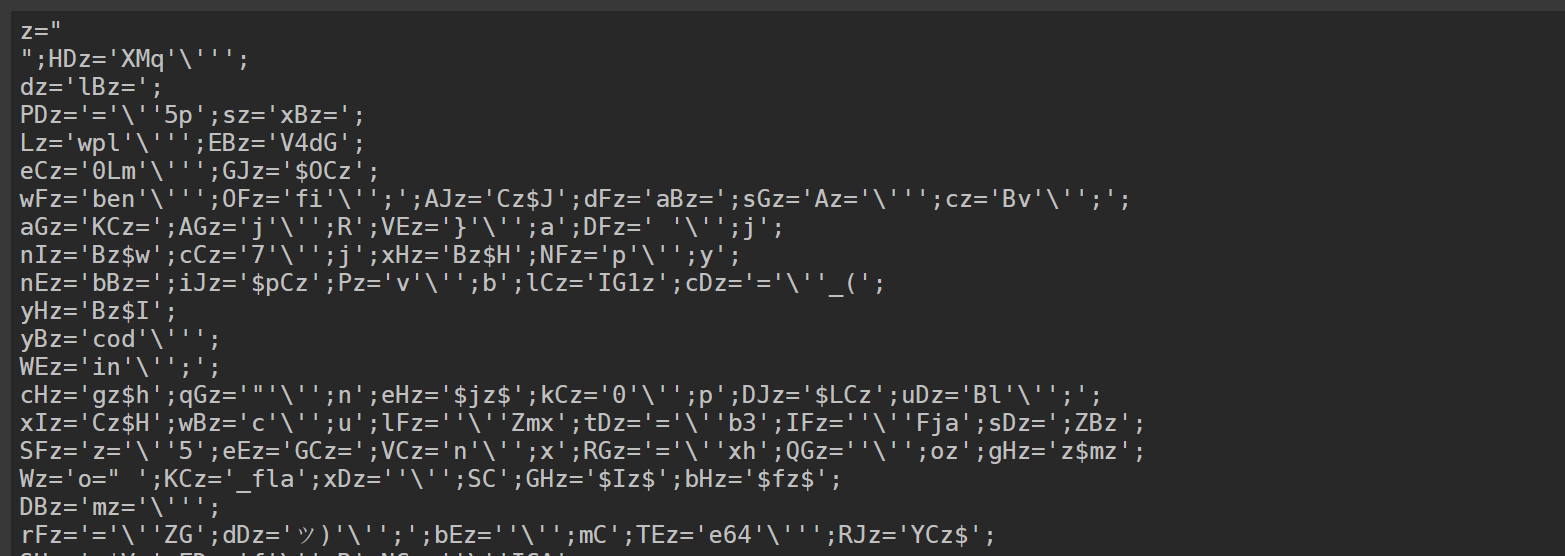
Uncovering the Domain and Flag Location:
After several iterations, the script becomes sufficiently deobfuscated to understand its content.
The script contains two base64 encoded strings. Decode the first string to reveal a domain name.
Decode the second string to find the URL where the flag can be obtained.
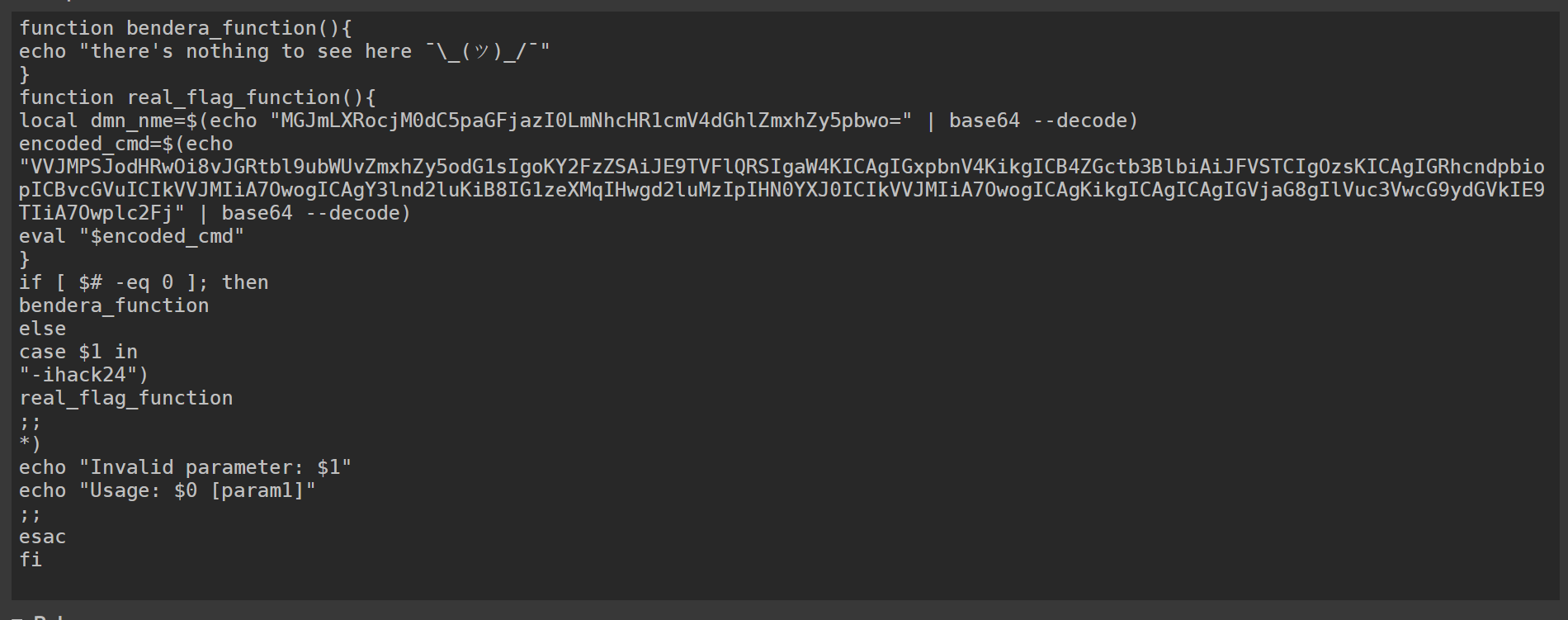
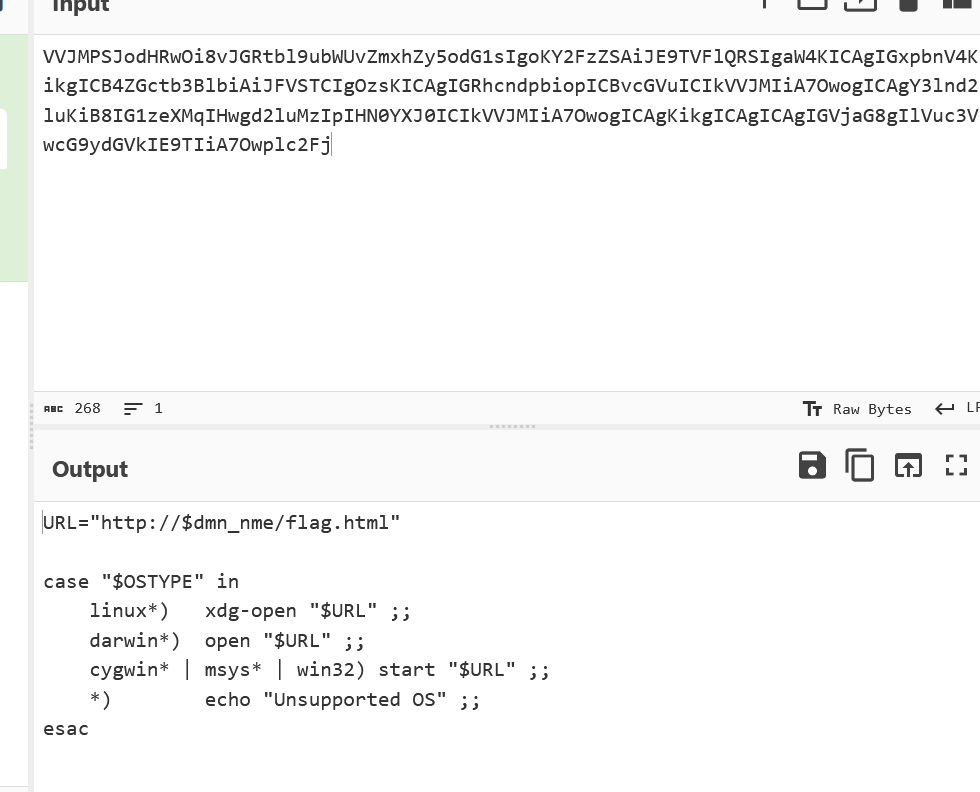
Retrieving the Flag:
Visit the webpage indicated by the decoded domain to locate and extract the flag.
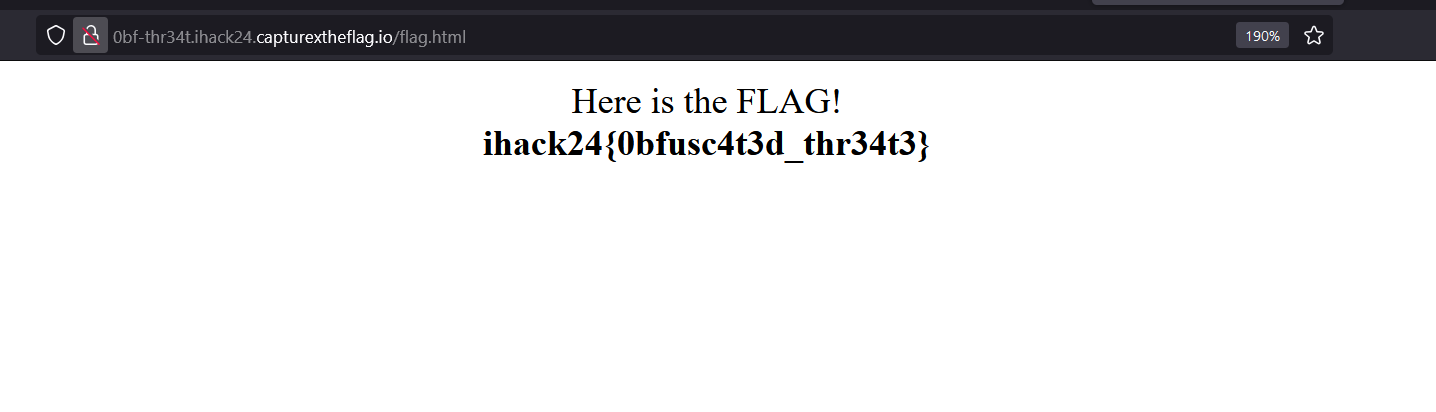
Flag: ihack24{0bfusc4t3d_thr34t3}