iamspeed
Challenge Information
- Name: iamspeed
- Points: 100
- Category: Reverse
- Objective: Analyze the Python-compiled executable to retrieve and decode the flag.
Solution
Initial Enumeration:
Upon inspecting the executable, it was identified as a Python-compiled executable based on the presence of Python-related artifacts.
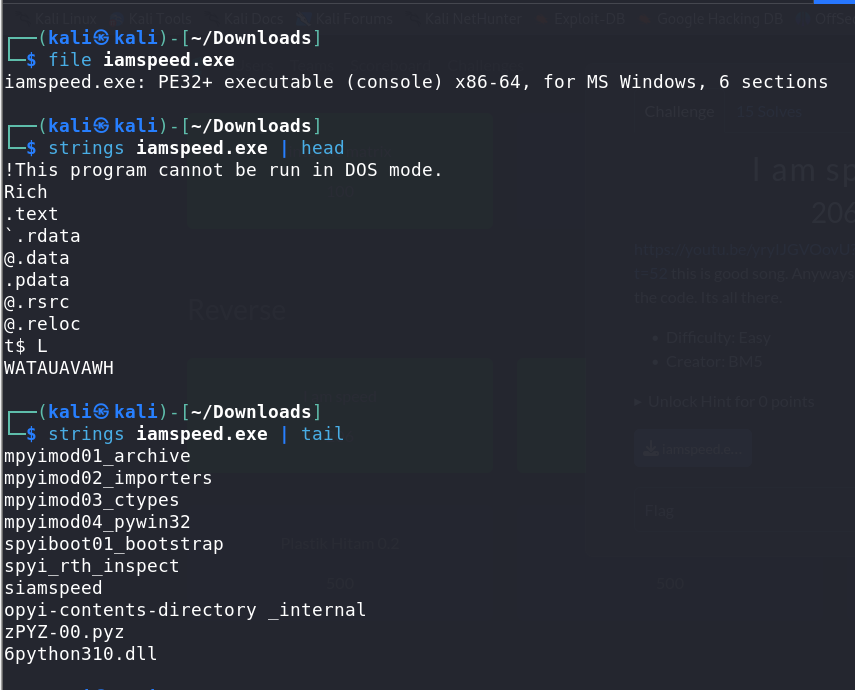
Decompiling the Executable:
Tools Used:
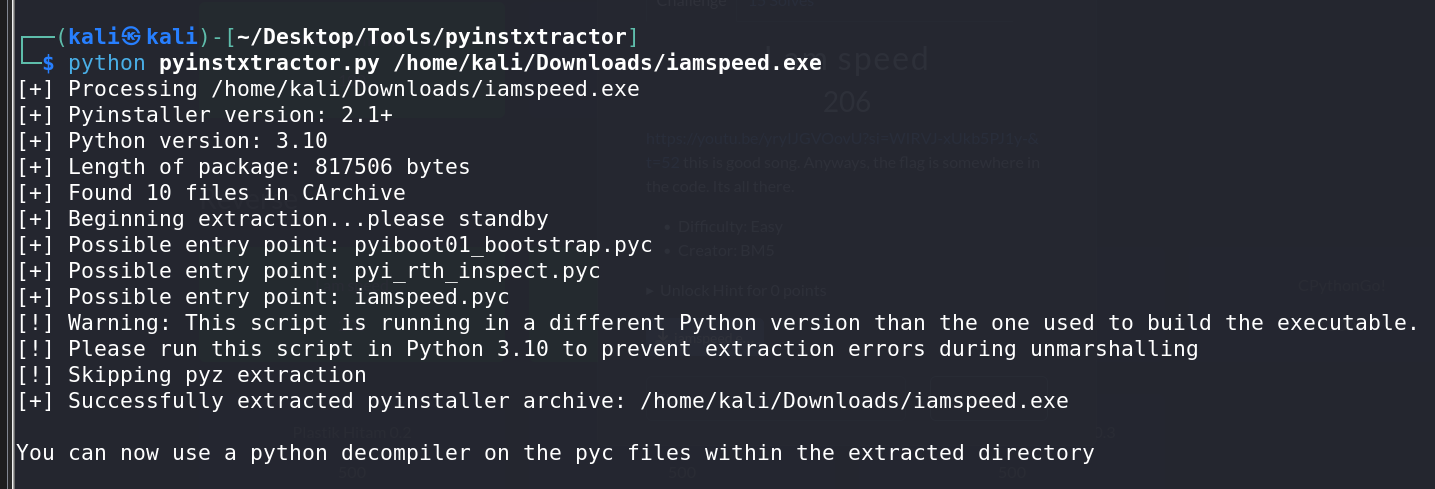
- PyInstaller Extractor (
pyinstxtractor) to extract the.pycfile. - PyCDC to decompile the
.pycfile into readable Python source code.
- PyInstaller Extractor (
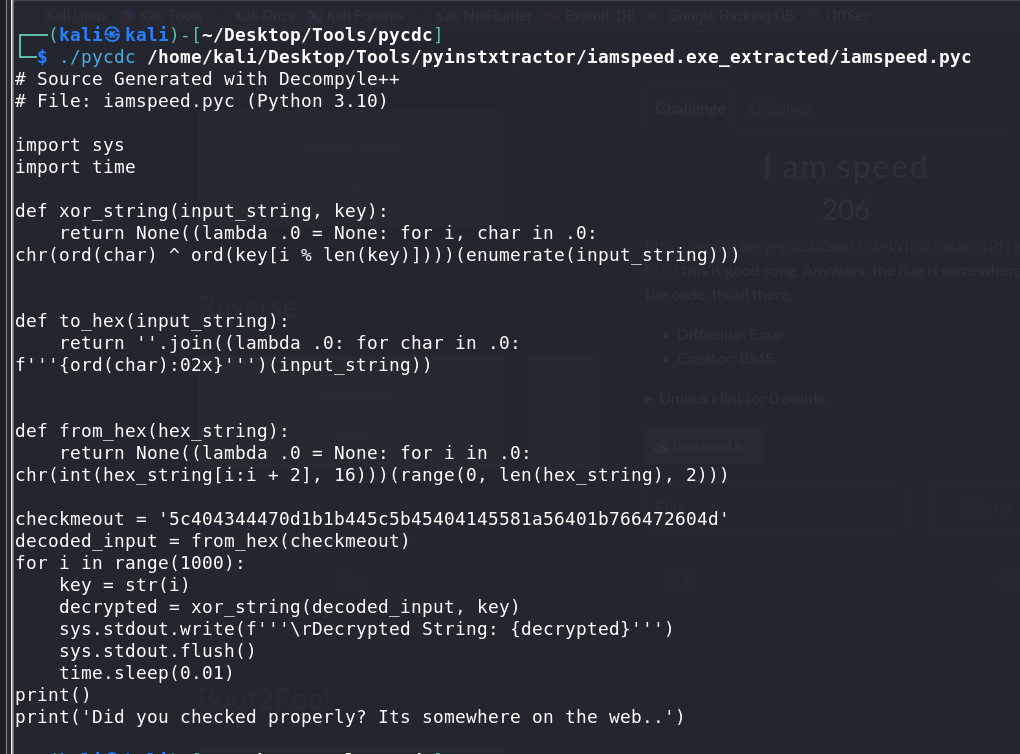
Analyzing the Decompiled Script:
My teammate, Nem4ros then ran the script and found hints of hidden HTTPS link.
He then modified the script to print the extracted link directly.
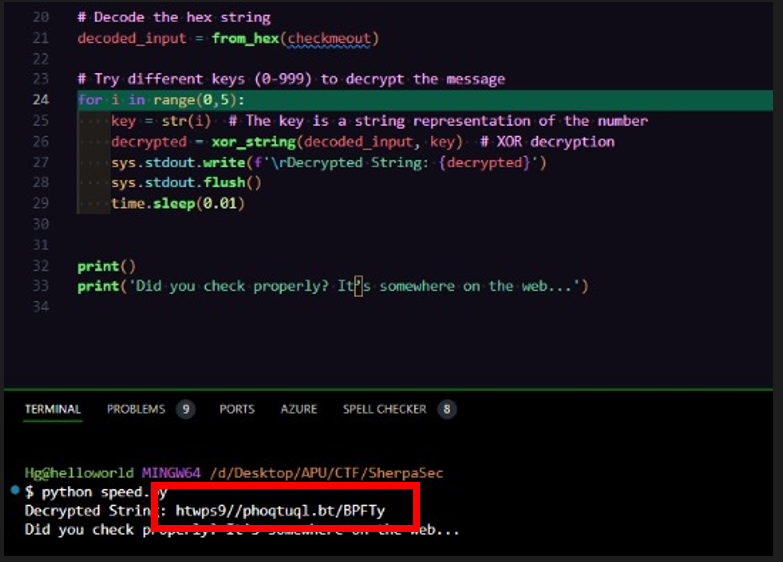
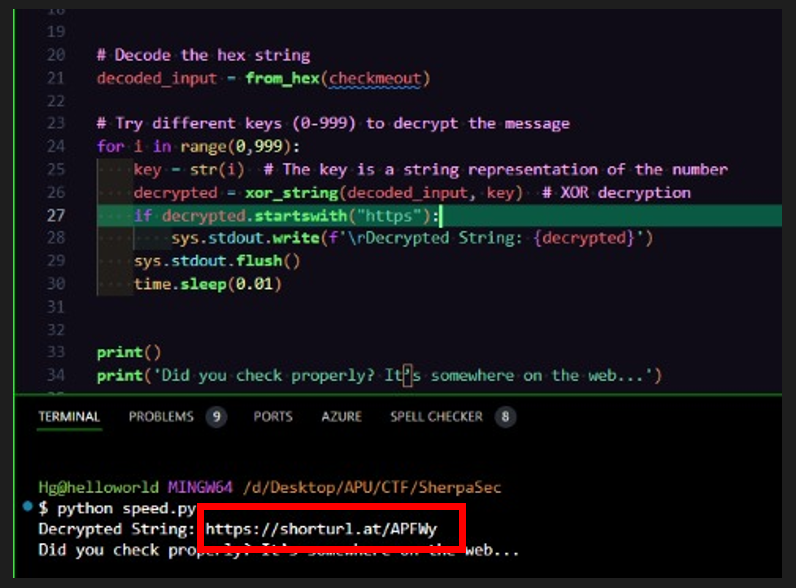
Accessing the Link:
The link pointed to a Google document containing encoded text.
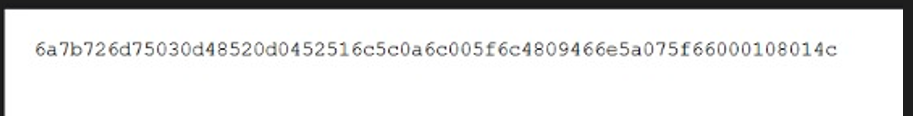
Decoding the Text:
Attempts to decode the text with standard methods like hex decoding failed.
The text was successfully decoded using the original script to process the encoded data.
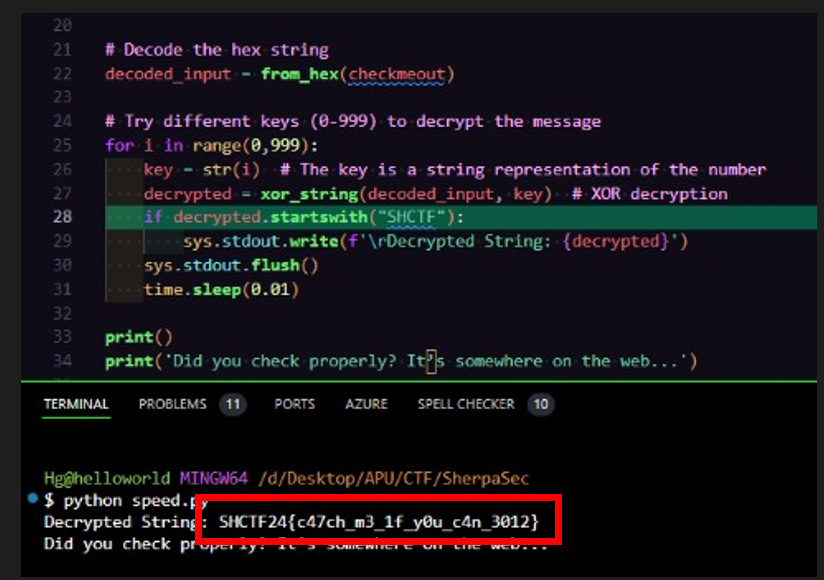
Flag
- Flag:
SHCTF24{XXXXXXXXXX}