Blink Logic CTF Challenge Writeup
Challenge Information
- Name: Blink Logic
- Points: 100
- Category: IoT
- Objective: Analyze a firmware file and determine the correct keypad input to unlock an IoT system running on Wokwi simulation.
Solution
To solve the “Blink Logic” challenge, follow these steps:
Challenge Setup:
The challenge provides a compiled firmware file in
.hexformat and instructs the user to simulate an IoT project using Wokwi, a popular online Arduino/IoT simulation platform.The goal is to determine the correct key combination on a virtual keypad to “unlock” the system and retrieve the flag.
Converting the Firmware:
Started by converting the
.hexfile into a binary format using theobjcopytool:1objcopy -I ihex BlinkLogic.ino.hex firmware.binThis step makes it easier to inspect the raw data inside the firmware.
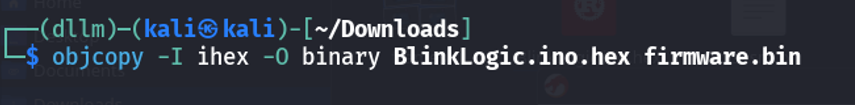
Static Analysis:
Ran the
stringscommand on the.binfile to extract human-readable content.1strings firmware.binAmong the output, several familiar keypad characters were visible (
123A456B789C*0#D), which appeared to represent a standard 4x4 keypad layout.
Identifying the Flag:
- Noticed an unusual string near the end of the readable content:
630B. - This did not match the keypad layout directly but stood out from the rest of the data — suggesting it was the intended key sequence.
- Noticed an unusual string near the end of the readable content:
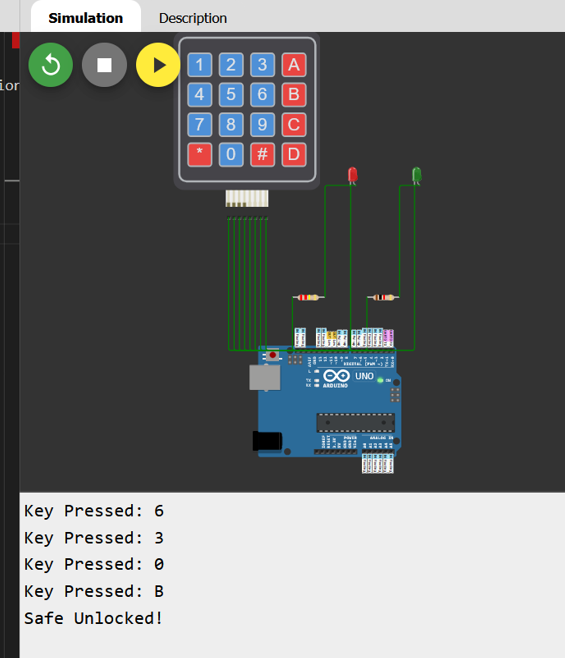
Testing the Key on Wokwi:
Loaded the given project on Wokwi and manually entered
630Bon the virtual keypad.The system responded with an “unlocked” message, confirming the key was correct.
Flag
netsa{630B}