BlackHole CTF Challenge Writeup
Challenge Information
- Name: BlackHole
- Points: 380
- Category: Web
- Objective: The objective of the BlackHole challenge is to find the flag hidden within the URL or the web page’s content.
Solution
To solve the BlackHole CTF challenge, follow these steps:
Initial Assessment:
- Identified that the challenge seemed the same as the preliminary one.
Script Adaptation:
Utilized a script from a writeup from that day.
Adapted the script to suit my needs for the challenge.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54import requests from bs4 import BeautifulSoup from urllib.parse import urljoin, urlparse, unquote visited_links = set() def get_links(url): try: response = requests.get(url) soup = BeautifulSoup(response.text, 'html.parser') links = soup.find_all('a', href=True) return [urljoin(url, link['href']) for link in links] except requests.exceptions.RequestException as e: print(f"Error retrieving links from {url}: {e}") return [] def is_directory(soup): return not "No directories found." in soup.get_text() and soup.find_all(class_="directory-link") def visit_links_recursive(url): if url in visited_links: return parsed_url = urlparse(url) base_domain = "blackhole.ctf.rawsec.com" if parsed_url.netloc != base_domain: return print(f"Visiting: {unquote(url)}") try: response = requests.get(url) soup = BeautifulSoup(response.text, 'html.parser') if is_directory(soup): print(f"Directory found: {url}") visited_links.add(url) links = get_links(url) for link in links: visit_links_recursive(link) except requests.exceptions.RequestException as e: print(f"Error visiting {url}: {e}") def main(): starting_url = 'https://blackhole.ctf.rawsec.com/' visit_links_recursive(starting_url) if __name__ == "__main__": main()
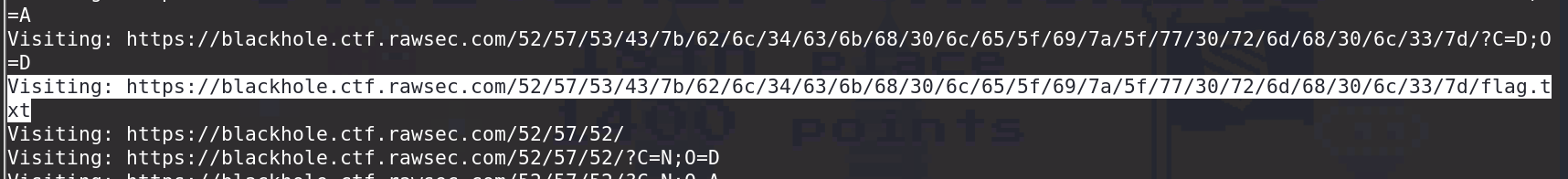
Flag.txt Extraction:
Used the adapted script to find a flag.txt file.
However, the flag was not directly found in the flag.txt file.
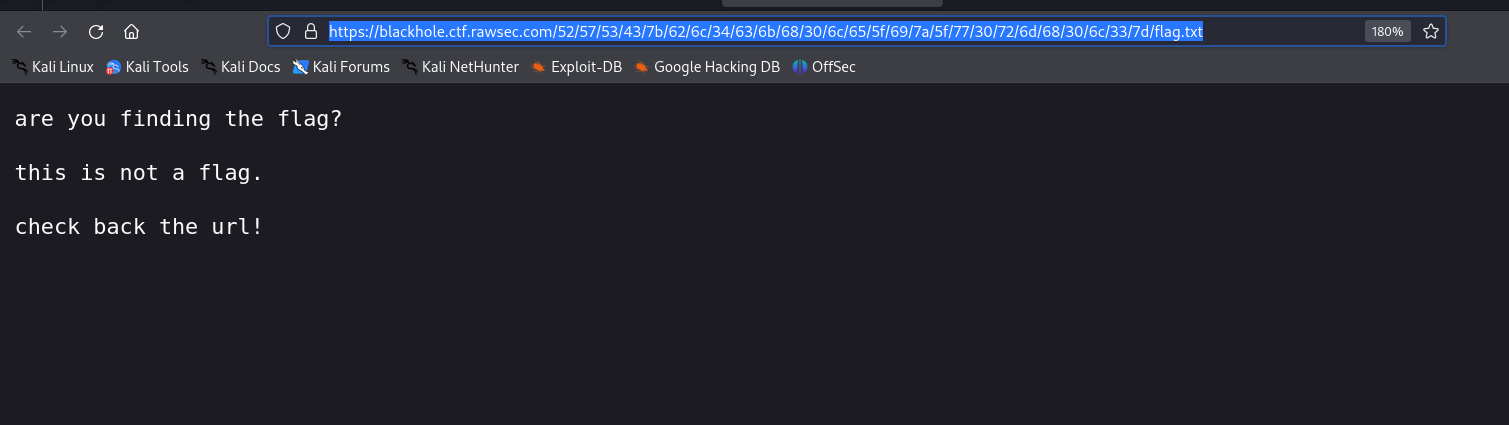
Rereading the URL:
Revisited the challenge’s instructions to reread the URL.
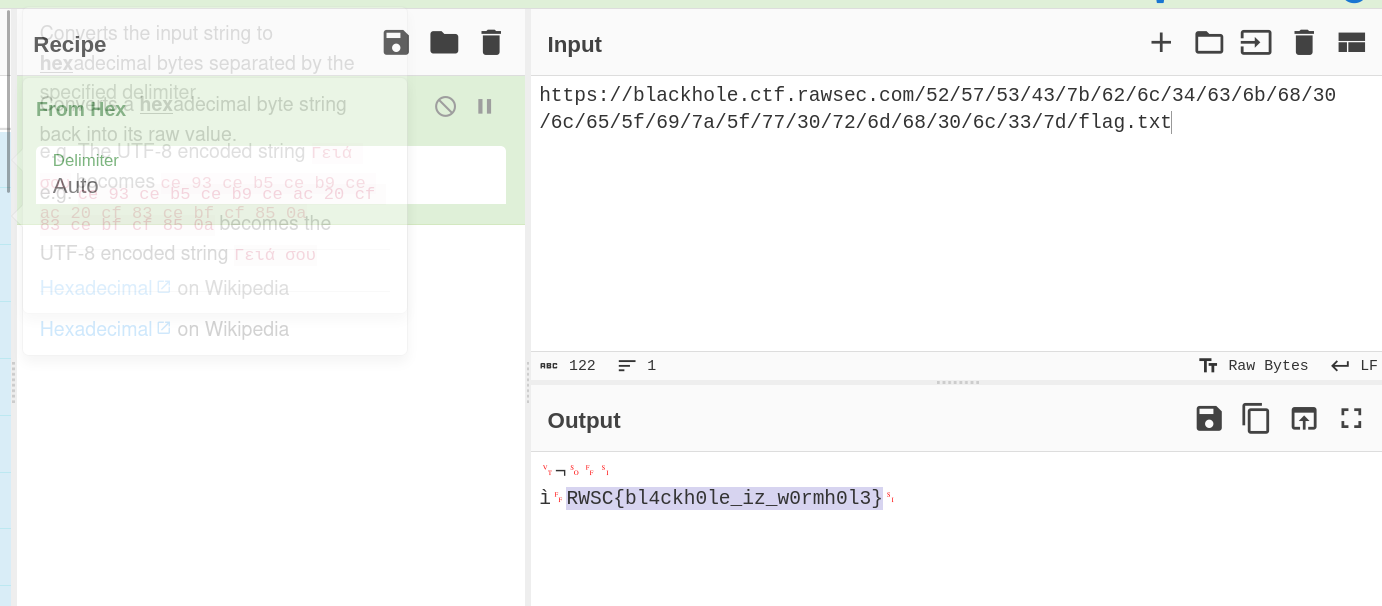
CyberChef Analysis:
Analyzed the URL using CyberChef.
Discovered the flag hidden within the URL.